Greg Ellifritz recently wrote a post about the phrase, “I’m in fear for my life.” In it he concluded that saying (which is not the same thing as being) you are in fear for your life is, “not a shortcut to provide some sort of instant justification for shooting someone.” I recently got a comment on one of my other blogs (the “gun blog”) that I’m going to talk about today because it is another great example – though a less common one – of ‘self-defense law folk lore.’
ProtonMail Five Years Later, Part III: Security Features
I have been using ProtonMail full-time for over five years, and recommending it for almost six. My contact form forward emails to a ProtonMail account, and any of you that have interacted with me have done so through ProtonMail on my end. A lot has changed since ProtonMail’s beginnings. This post will cover the basics of ProtonMail: how it encrypts your data-in-motion, data-at-rest, and some other features.
ProtonMail Five Years Later, Part II: Tiers & Paid Features
I have been using ProtonMail full-time for over five years, and recommending it for almost six. My contact form forward emails to a ProtonMail account, and any of you that have interacted with me have done so through ProtonMail on my end. A lot has changed since ProtonMail’s beginnings. This post will cover the basics of ProtonMail: how it encrypts your data-in-motion, data-at-rest, and some other features.
Apricorn Aegis Fortress L3 Secure SSD
I recently reviewed the Apricorn Aegis SecureKey flash drive and was extremely impressed with its security features. More recently I’ve had the opportunity to work with the Aegis Fortress L3 Secure solid-state drive. Today’s article will take a look at this device.
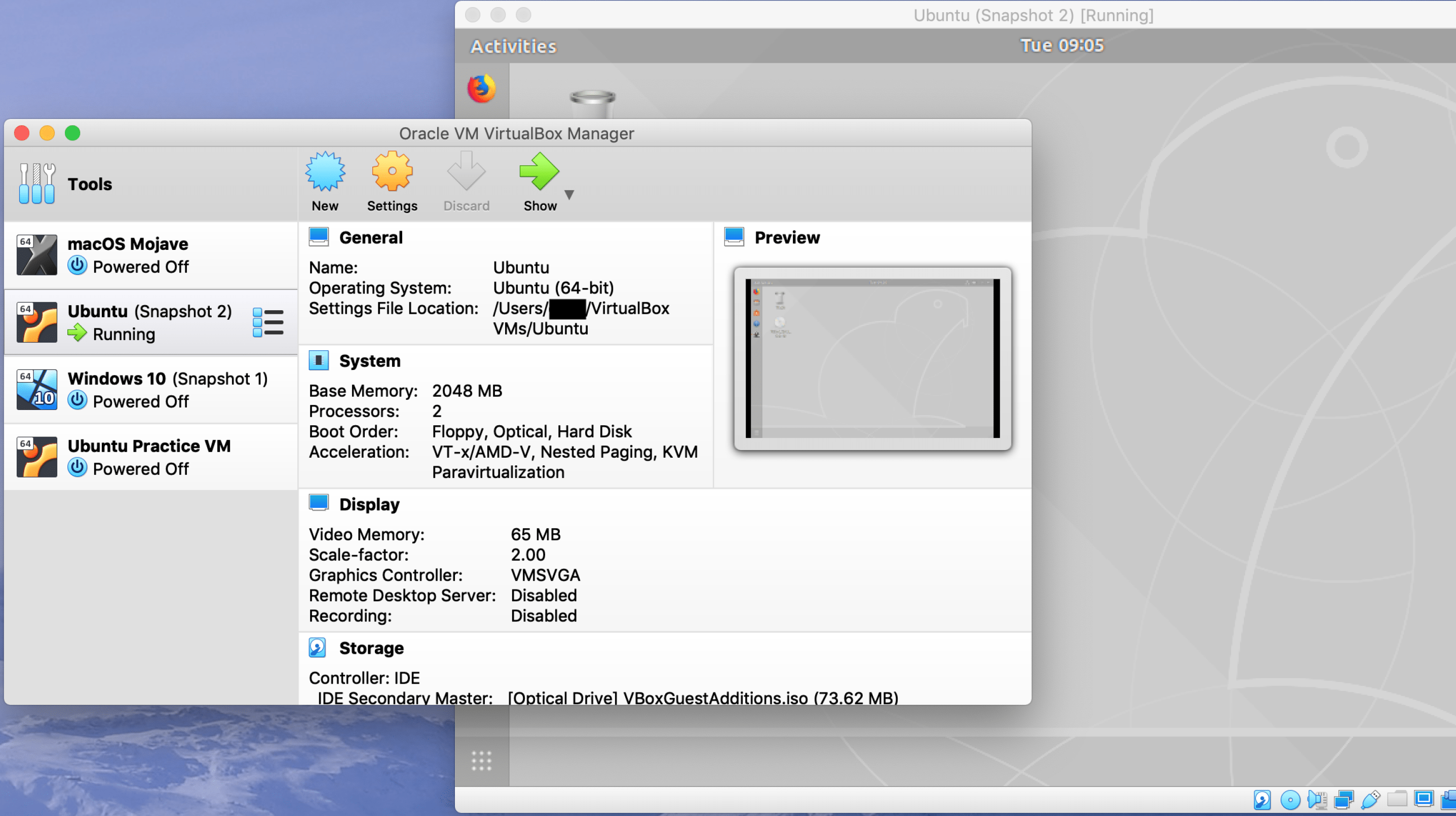
VMs Part 2: Installing and Updating Ubuntu in VirtualBox
In the first part of this series I discussed how to create a virtual machine using VirtualBox and Ubuntu. Today we are going to execute several steps to get Ubuntu installed, updated, and make it just a bit more functional. I we will finish by discussing how to shut down a virtual machine.
ProtonMail Five Years Later, Part I: The Basics
I have been using ProtonMail full-time for over five years, and recommending it for almost six. My contact form forward emails to a ProtonMail account, and any of you that have interacted with me have done so through ProtonMail on my end. A lot has changed since ProtonMail’s beginnings. This post will cover the basics of ProtonMail: how it encrypts your data-in-motion, data-at-rest, and some other features.
VMs Part 1: Creating Your First Virtual Machine
It recently occurred to me that in over five years of running this blog, I’ve never given step-by-step instructions for setting up or using a virtual machine (VM). It is likely that a lot of you already use VMs don’t need a tutorial. If that applies to you, please share this with a friend who does. It is equally likely that some of you could use step-by-step instructions. This tutorial will cover creating your first virtual machine.
OPSEC for Legal Marijuana Consumers
The commercial sale of legal, recreational marijuana in the United States poses some interesting legal problems. Marijuana is completely legal under the laws of some states, but still a Schedule I substance according to federal law. Though the strange detente that has emerged over the past several years has kept things awkwardly civil, the federal government would be legally justified in cracking down on growers, purveyors. . . and consumers.
Basic Alarm System Best Practices
An intrusion detection system (IDS) system should be an integral part of your home security plan. IDSs are detective security measures that also have a great deal of deterring value. Alarms are far more complicated than most people realize, however. To provide the maximum intended effectiveness, alarms must be carefully installed, tested, and used. These alarm system best practices will help you assess your own system or provide some guidance if having a new one installed.
The Apricorn Aegis SecureKey Flash Drive
The Apricorn Aegis family of flash drives, HDDs, and SSDs has been around for quite a while. I’ve generally rejected them based on price alone. Recently a customer requested training that included this drive. Since learning the Aegis and its capability, I’m very impressed. If you have compelling data security needs, this product might be for you.