Few among us would knowingly hand out copies of our keys to strangers. Many of us do, however, provide strangers with all the necessary information to generate a working copy of our key(s). Within two minutes of scanning this site I found at least half a dozen unredacted photos of common, residential keys – bad business. A few weeks ago I told you I would explain why posting pictures of your keys is a bad idea. Here it is.
This article contains affiliate links.
This article was originally written by me and published on another of my blogs on October 11, 2015. I have added a great deal of information and photos, and greatly expanded the section on protecting yourself from these types of attacks. If any part of this article is unclear, please contact me – my goal is to share knowledge, not hoard it.

A key contains a certain code that is unique to your lock, “secret” information that allows your key to open your lock and only your lock. This information should be protected. Leaving keys in plain sight, posting photos, or allowing physical access by untrusted persons allows an attacker the opportunity to capture the information necessary to copy your key.
Key Profile
First, it is important to understand the pieces of information necessary to generate a key. They are the key profile, the number of cuts, and the depths of each cut. I discussed each of these in great detail in my recent interview on the Uncensored Tactical podcast. All of this information is available from the lock itself by a sufficiently skilled attacker, but the information is much more easily acquired from the key. If you’re interested in learning key generation, I STRONGLY recommend Deviant Ollam’s outstanding Keys to the Kingdom: Impressioning, Privilege Escalation, Bumping, and Other Key-Based Attacks Against Physical Locks.
The key profile is the shape of the keyway into which the key is inserted. This information is important because it dictates which key blank must be used to generate a key for that lock; if the key cannot fit into the keyway, it will not operate the lock. There are several ways the key profile may be obtained. First, it may simply be stamped on the key bow (the portion of the key used for turning) in the form of a code like“KW1” for Kwikset and it’s knockoffs, or “C” for Schlage keys

If it is not stamped it is usually fairly easy for an attacker to make an educated guess. The photo below depicts a Kwikset key alongside the keys for three aftermarket locks. Each of these locks utilize Kwikset specifications and the bows of each are a similar shape. An attacker seeing a key bow of this shape could be reasonably certain of the keyway and the necessary blank (KW1).

The photo below depicts a common Schalge “C” keyway. The contours of the keyway require matching a key blank. This is designed to keep you from putting any old thing into the key way.

Number of Cuts
Once the key profile has been ascertained, an attacker must determine the number of cuts. The attacker can make an intelligent guess as the vast majority of locks (at least in the US) adhere to the following protocol: residential locks usually have five pins while commercial locks are generally more likely to have six. The attacker doesn’t have to leave this to guesswork, however.
The cuts on keys are what we generally misunderstand because we usually have no idea what we are looking at. The important information in a key is the flat cut beds (the “valleys”) on the key. Each valley is where a pin will sit when the key is fully inserted into the lock. Simply counting the cut beds in the key will yield the number of cuts. In some cases referencing manufacturer’s specifications can also be helpful; some manufacturers may offer certain locks in only five- or six-pin configurations. The photo below shows the five cuts on a Kwikset-style key.

Depth of Cut
Referencing manufacturer’s specifications can also help us with the last step, determining the depth of each cut. The key profile and number of cuts are not considered the “secret” information in the key. The unique combination of cut depths is, however, and this information is what makes your key different from those of your neighbors’. This is the information that gives your key its unique code and as stated early in this article, allows it to open your lock while preventing it from opening others.
The cut depths are described in what is called a key code. In Kwikset locks, for instance, a “1” cut will be the shallowest possible cut and a “6” will be the deepest possible cut according to manufacturer cut specifications. These cut specifications are widely available. The screenshot below was captured from a locksmith’s website (insecure link), and the site hosts pinning specifications for long list of other manufacturers.
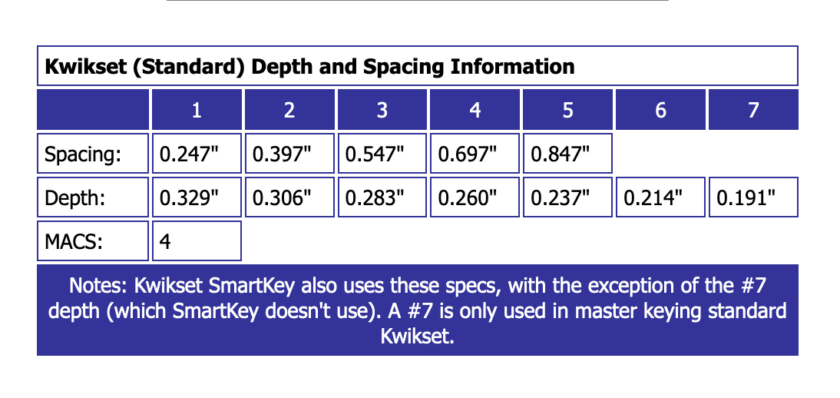
There are several ways that an attacker may acquire the key code; obtaining a direct code, “sight-reading”, or measuring the key. Once the key code has been obtained, this information can be input into a key machine to produce a working key.
Obtaining a direct code is by far the easiest method of obtaining a key code. On OEM (factory) keys, this code is frequently stamped on the bow of the key. The direct code consists of a five- or six-digit number, each correlating directly to a cut position and the depth of cut in that position. The key in the photo below gives up all its secrets at a glance. The shape of the bow is indicative that the key uses a KW1 key profile. Secondly, there is a direct code stamped on the bow, the numbers “36645”. This gives us the number of cuts (5) and the depth of each cut—everything we need to cut an operating key for the lock.

If an attacker is sufficiently familiar with the system, he may not even need to see a direct code. He can compare the cuts and make a reasonable determination of the depth of each, a technique called “sight reading”. It is this technique that is perhaps the most dangerous because all it requires is a quick look at your keys (or worse, a photo – DON’T POST PHOTOS OF YOUR KEYS ONLINE!). The photo below demonstrates the relationship between the number in the code and the physical depth of cut. It also serves to talk about how reading a key works: the “3” cut in the first position is shallower than any other cut, but is obviously fairly deep relative to the possible height of the key blade. The other three depths represented on the key (6 in positions 2 and 3, 4 in position 4, and 5 in position 5) are all incrementally deeper than each other.
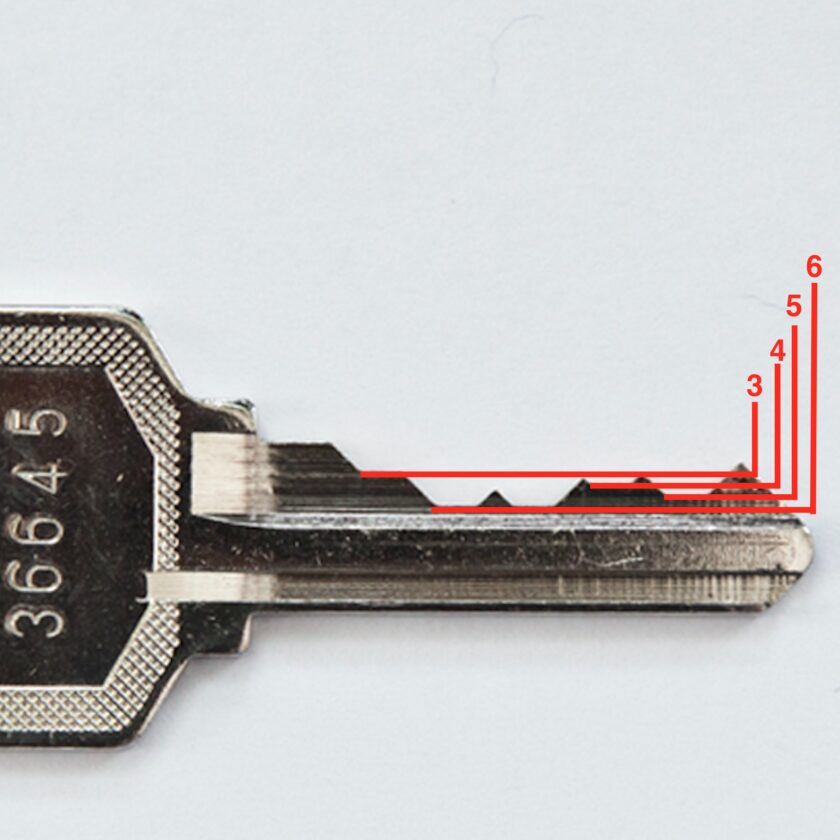
There is also another clue that can help us out. Look at the photo below (same key, just with the distracting red lines removed). Notice how deep the two #6 cuts are. The are almost down to the first contour of the key. On Kwikset and Schlage keys (and many others) cuts will not extend deeper than this first contour line. This is a very strong indicator that those cuts are #6 cuts, giving us one number to base our guess upon. Note that this is not true on some keys, like Yale.

This post is mainly about posting pics of your keys online. However, if an attacker has even very brief physical access to your keys he can easily measure the depth of each cut. One such tool is a simple gauge, about the size of a credit card, like the one shown below.

To use this tool, determine the correct pinning specification (Kwikset, Schlage, etc.). Insert the key into the correct gauge and measure each cut position. This is a very fast and easy way to “decode” a key, and this tool is available on Amazon for under $15.

The Patch
I sincerely hope this has influenced you to be a bit more careful with your keys. If so, there are some simple measures you can take to prevent key-duplication attacks.
- Keep your keys out of sight. Keep them in a pocket, a purse, or use a pouch that keeps them covered, and never, ever post pictures of you keys online!!! If you simply can’t resist photographing and posting your keys, get a set of dummy keys specifically for the purpose. Likewise, don’t leave your keys unattended; all too often I see people leave their keys lying on their desks, etc.
- When giving keys to a valet, mechanic, or anyone else who requires your car key, only give them the car key. There is no need to give out your house key, mailbox key, and office key to someone who only needs access to the car. Additionally, some cars offer mechanical keys that are designated as valet keys which are specially cut to operate the door and ignition, but not storage compartments such as the glove box and trunk. If your car has one, use it.
- When giving keys to service personnel who require repeated access to your home such as dog-walkers, babysitters, cleaners, etc., inquire about their company’s policy regarding keys. Look for a service provider that has a policy offering rekeying of your locks if they lose your key.
- Never leave a key hidden outside your home. If someone finds the key he or she may simply steal it. Theft is the best case scenario because you know it is gone the first time you look for it (though this may be weeks or months later) and can change your locks. The worst-case scenario is the attacker duplicating your key and replacing it; now, not only does the attacker have a key, but you have no idea that he does.
- Have your keys cut on “neuter-bow” blanks (ask an actual locksmith). These are blanks that have a non-descript bow that does not bear the key profile code, does not have a distinctive shape that could reveal information, and is certainly not stamped with a direct code. Further, most neuter-bow keys also bear the warning, “Do Not Duplicate” which may provide a very small measure of protection against unauthorized duplication (don’t let this give you a false sense of security about passing out your keys; many locksmiths and retail locations will still provide duplicates of so-called DND keys).

- Purchase and install UL-listed high security locks. Most high-security keys have unique, novel mechanisms that are very difficult to copy. They are also usually patented and the key blanks are only available to authorized dealers. Further, to have a duplicate made, a special key duplication card is often required along with a photo ID. Finally, some high security mechanisms have a moveable element within the key. If this element (specifics vary) cannot or does not move it simply will not operate the lock. Because this type of key is so complex there is very little chance of an attacker manufacturing an improvised blank upon which he can copy your key.

Real World Example
In 2015 a rare news item highlights this danger. The Washington Post published a story about the TSA, and in it included a photograph of a set of TSA luggage keys. These keys are a declared backdoor in TSA-approved locks, allowing officers to inspect bags but, theoretically, keeping the bag secured from everyone else. The posting of the photo became a story itself because of the easy ability to reproduce keys from a photograph. The photograph of the keys no longer appears on the Washington Post, but very good photos are available here and here, and CAD files are available here, if you want to 3D print your own set.
Develop Your Skill
If you want to deep dive into this without purchasing Keys to the Kingdom, there’s some fantastic reading HERE (opens to .pdf). It focuses on duplicating keys from photos, and goes into much greater detail than I have. It would be worth your time to read. Additionally, since we’re all doing “social distancing” because of coronavirus, you might have some spare time in the next few days and weeks. Here’s some guided practice to keep you busy.
Below are photos of five keys. The two Kwikset-style keys are pretty easy to decode. If you want to email me to verify your results, hit me via the contact form (if you’re wrong I’m just going to tell you you’re wrong, not give you the answer). Seriously – don’t hesitate to shoot me an email, I really enjoy the interaction.

The Schlage keys below will be a bit more challenging. You’ll have to dig up Schlage’s pinning specs (it’s not that hard, I’ve already given you a link in this article), and with 10 potential cut depths Schlage is a bit harder anyhow. Again, feel free to hit me up to verify your numbers.



Once you decode all of these, hit up some EDC pocket dump sites and threads. Good luck!
Image Attribution: Featured Image by Brett Hondow from Pixabay





1 thought on “Don’t Post Photos of Your Keys!”
Comments are closed.