In my last post in this mini-series, I talked about Step 1 in my Security Framework: Malware Resilience. The steps there are all designed to minimize the chances of contracting malware. There are other steps, more advanced that can be taken, and maybe I’ll cover those in the future. They get much more technically demanding and time-consuming to implement.
Note: this series of articles has been extremely unpopular. This baffles me. Most of you probably know more about guns, shooting, prepping, etc. than I do. None of you know nearly as much about this topic as I do; I’ve written six books on it, and I am paid very well to develop curriculum and teach this very information to to special operations and intelligence community personnel. This information impacts your daily life, your finances, and the safety of you and your families. I challenge you to spend some time with the things you aren’t already knowledgeable and skilled in. So…I’ll ask you guys: would a webinar format be better for this? I would gladly teach this as a class, live, on some sort of webinar platform if there is sufficient interest, let’s say 4-8 people. Thoughts? Hit me on the contact form.
Part I | Part II | Part III | Part IV.1
I’m often asked how the average person gets some bang for their buck. The steps listed in the last post (1. get off your admin account, 2. update, update, update!, and 3. antivirus) are good examples of very high “flash to bang” steps. They take minimal effort to enable, require minimal effort and interaction on a daily basis but provide a significant upgrade in most people’s security. Every human should do those three steps.
Now I’m going to go out of order and talk about Step 2 of the framework: Protecting Cloud Stored Data. My framework is ordered to apply to the operational context of most of my government clients. For our purposes here, protecting cloud-stored data is probably the next most important item. For the average citizen, this is a massive concern. Everything is cloud-connected. Our online accounts exist in enemy territory. They can be “touched” by anyone who wants to take a crack at logging into them.
Protecting Cloud Stored Data
A lot of people think because that a lot of information is already “out there,” then some of these methods are moot, or even a waste of time. A friend of mine (let’s call him Bill) once mentioned that because of the information submitted to get his security clearances, paying for his blog, and his normal pattern of online behavior, his information is “already out there.” And that’s true – that information does exist in the nebulous “out there.”
But that doesn’t mean we shouldn’t care about it. Because it exists somewhere doesn’t mean it is available everywhere to everyone. We should take personal responsibility and ownership for it and protect it to the fullest extent possible. We’re all already doing this to some point whether we realize it or not.
Back to Bill an example (sorry, Bill). Yes, you’ve given OPM* your social security number, DOB, and mother’s maiden name, but you probably aren’t posting that information on your Instagram page. You might’ve given your web host your credit card number, it’s expiration and CCV, but that information probably isn’t something you would put in a forum post on arfcom. Subconsciously we recognize that just because information exists about us, it isn’t and shouldn’t be available to everyone, everywhere.
The purpose of these next few steps is to protect that information. We protect it by making as difficult as possible for unauthorized parties to access. In the examples above OPM, our web hosting provider, our our Instagram followers are authorized parties. Still, we don’t give all of them everything.
Step One: Limit the Scope of Information ‘In the Wild’
Once again we’re going to focus on behavior rather than tools. Whether we realize it or not, we have a massive ability to control information that is “out there” about us. There are a few steps we need to take to do that.
Delete unnecessary information in your accounts. Still have that Flickr account that you don’t use anymore? You should probably delete those photos (you really should; Flickr is now owned by Verizon…and trust me that’s bad). Still have that old Yahoo! email account you used in high school? You REALLY need to delete the information in that account. “But, Graveyard, why? I haven’t used that account in years!” I’m glad you asked.
If you’re my age (late 30s/early 40s) that Yahoo! account probably contains old Amazon orders. It probably contains appointment information, flight itineraries, information about your vehicles, your bills, etc. It also probably contains emails to and from old flings. Though it doesn’t feel like it, that information is really, really important – not to you, but to a bad guy. Think about this:
If I wanted to conduct a social engineering attack against you, all of that information would be incredibly useful. I could craft an email to you as your college girlfriend. I admit, even I would probably fall for that one, and you would, too whether you admit it or not. I could craft any number of emails that almost anyone would either respond to, or be compelled to click a link in. My advice: CLEAN HOUSE! Delete all those old emails from the accounts you no longer use. That information can now pretty much ONLY be used for a purpose that is not in your best interest. This goes for current accounts, too – don’t leave more information in them than you absolutely need to.
Delete Old/Unused Accounts. After your content is deleted, there’s no reason not to delete your old/unused accounts. If they don’t exist, they can’t be hacked. Though they might not represent a huge threat to you, they can be used to trick your friends and family. If you cannot delete the account, delete all the content it contains (or change that content to purposely misleading information) and lock it down to the fullest extent possible by following the remaining steps in this post.
Think Carefully Before Creating New Accounts. Read (OK, at least skim) the privacy policy. Do you need to provide true and accurate information? Is this really a service you even need? Do you need iCloud, or can you get by backing up your phone to your laptop? Again, much of that information may already be with OPM or GoDaddy or Facebook…but that doesn’t mean you need to give it to ten other services. If you can avoid it, just don’t create/use the account in the first place.
Keeping minimal information online is our best bet at preventing hacking. We still need email, online banking, etc. Since we can’t minimize everything down to zero, we need a strategy to protect those accounts that are still out there. Now we get into the fun stuff…
Authentication Measures
Just kidding. Now we get to talk about everyone’s favorite: PASSWORDS (and other authentication measures).
Step One: Use Good, Strong Passwords. Here’s the bad news: all of the passwords you currently use suck. If you know them in your head and type them with your fingers, they suck. Period. They are difficult for you to remember and type, but trivially easy for a computer to break. Here are the three criteria for making strong passwords:
Length: This is absolutely the most important factor. Having special characters and numbers is important, but it pales in comparison to having a long password. Here’s why: if you follow my other two rules (below) you’ll automatically be opted out of the most common ways passwords are broken (simple guessing and dictionary** attacks). This means an attacker looking to get access to your account must resort to a brute force attack (attempting to test every possible combination of characters out to x-length). Every single character you add in length makes the problem of brute force take exponentially longer. My recommendation generally is attempt to make all passwords 30 characters or longer. Yes, I know that is a lot, but I will recommend some tools to help with that.
Complexity: Although less important than length, complexity is still important. This means using at least one character from each of the following groups: uppercase letters, lowercase letters, numbers, and special characters (!@#$%^&*()_+, etc.). You don’t have to go nuts here; you just need at least ONE of each. This forces an attacker to add all of those ingredients to his formula when conducting brute force. Again, this has an exponential impact on the time it would take to find YOUR password.
Unpredictability. Humans are predictable. We reuse the same passwords over and over, or modify them only slightly. We make passwords in predictable ways (i.e. adding a number to the end of a simple word, or replacing a letter with a special character as in, “p@ssword”). Predictability drives dictionary attacks (definition in footnotes below). If you are making a password up in your head, even if you have never used it before, it is almost certainly predictable.
Password Management Tools
There is one other factor when it comes to passwords: you should use a different one on every. Single. Account. Period. No “ifs,” “ands,” or “buts.” I know at this point you’re asking, “how am I supposed to remember a different, 30-character password that I didn’t make up in my head…for every single account?
Step One Point One: Use a Password Manager. A password manager is nothing more than a simple application or utility that remembers all your passwords securely. They have a number of benefits: they take up minimal space, use minimal resources, are optimized for ease of use, and they help you do what computers are good at: remembering stuff.
There is an adage that goes something like, “security and convenience are inversely proportional.” This is usually true, but not in the case of password managers. They make your life easier. You never have to try and remember which password you used on that site you rarely visit. You never have to make up a password for a new site. Password managers do all this stuff for us. Even my girlfriend (who is not a tech geek, nor terribly interested in security or privacy) LOVES her password manager.
My two specific recommendations are:
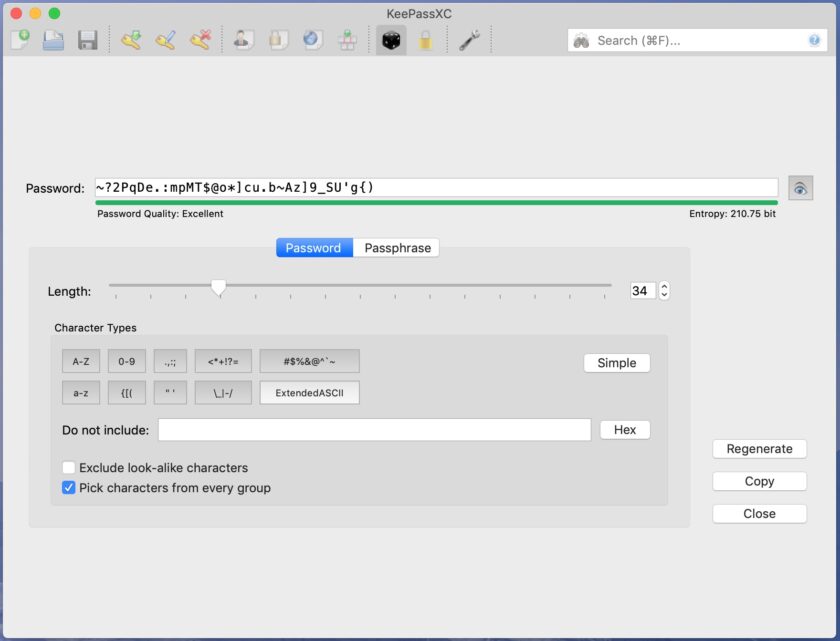
KeePassXC. The document posted in the first post in this thread recommends KeePass. I recommend KeePassXC (Google it) as the most secure password manager. It is updated much more frequently and has massively better options than legacy KeePass. Here’s how it works: the application creates a database on your computer. You assign a master password to that database (one of the very few passwords I actually know is the one to my KeePassXC database). Next, you create entries for your accounts that contain at a minimum the username, password, and URL, and there are other fields if you want to use them. When you close the database it is encrypted (AES-256, we’ll talk about that later) and stored locally on your device. You can create copies of this database to place on other devices or to store as backups. There are benefits and downsides to this system.
- Benefits: First, KeePassXC is completely free and open-source. It is more secure than the next system I will discuss. Your data doesn’t get transmitted to the “cloud”. It exists only on the machines you put it on. You have ultimate control and the best possible security story.
- Downsides: You have no version control. Let’s say you make a database and put it on your laptop and your wife’s computer. As long as you both know the password and have the application, both of you can open the database. So far, so good. But let’s say your wife logs into your bank account and it tells her it’s time to change the password. She changes it in *her* copy of the database. Guess what? Your version of the database doesn’t get updated – that’s the first problem. The second problem is that these databases only exist locally. If you only have the database on devices stored in your home and your house burns down…yeah, you can see where this is going.
LastPass. LastPass works differently; it is cloud-hosted. You first sign up for a subscription and download their browser add-on (desktop) or app (mobile). Much of the setup is similar in function to what I described for KeePassXC – create entries, add your accounts, etc. Everything gets encrypted locally, on your device, then transmitted to LastPass’s servers. This has a ton of benefits:
- Benefits: You have excellent version control; if anyone on your account (I wouldn’t share with too many people, but sharing within your family might be desirable) changes anything, the master database is updated and everyone’s instance of LastPass reflects the change. You have insane flexibility of function; you can create specific vaults (for instance, a vault with work passwords that you access from your work computer, or a vault for your kids that contains only items they are allowed to log into). LastPass even has an emergency option that lets you set up a designated recipient of your passwords in the event of your death (you are not required to use this option if you don’t want to). LastPass is also very secure and has an excellent reputation.
- Downsides: though very secure, LastPass isn’t quite as secure as KeePassXC. Your data is still transmitted across the internet (albeit in an encrypted state) and your account is accessible through the internet. To get access to premium features and access LastPass from multiple devices you also have to pay for it (~$3/mo).
I If there’s one big takeaway from this long post, it is: use a password manager and begin changing your passwords. However, DON’T RUSH IN and try to change everything!!! Get the password manager and put a trial password in it (the one you know, in case you screw something up). Get familiar with the functions and cycle of operations. Get really comfortable before you start changing your passwords to long, complex, pseudorandomly generated junk. Take it nice and slow.
I know this one has run long, but I have one more step:
Two-Factor Authentication
Two-Factor Authentication (2FA for short from here on out) is a system that requires two “factors” to log in to a system. The first is a knowledge-based factor: your password. The second should be a different factor, like a one-time code you retrieve from your phone.
2FA makes you massively more secure than a password alone. Let’s say you are using amazing passwords from your KeePassXC database. That’s great, but the service could still spill their database of passwords somehow – you have no control over that. But even armed with the correct username AND password, an attacker would still need that “other” factor to be able to log in to your account. Another example: you use a public computer/work computer/malicious Wi-Fi network where your information is captured. Well, it’s not great that they got your password, but without access to that other factor, it still won’t do them any good.
There are several ways 2FA works. I’m only going to talk about the two most common:
SMS. All of you are probably familiar with this one. You log in, then you get a text message with a six-digit code. Here’s the deal: that is way better than nothing, but it’s no ideal. There are a million ways that text can be intercepted (in fact, NIST [the National Institute of Standards and Technology] “deprecated” SMS two-factor all the way back in October of 2016). Also, if you ever travel and don’t have cell service, you simply aren’t going to receive that SMS. However, if you have an account and the ONLY two-factor option is available is SMS, IT’S WAY BETTER THAN NOTHING!!! Use it!
Software Token. This is a massive security upgrade over SMS, and the technique I use for most things. Software tokens are widely used; off the top of my head Amazon, Dropbox, Evernote, Google, LastPass, SquareSpace, WordPress…and about a million more sites allow software tokens. Using it requires a smartphone and an app. The app I use and recommend is called “Authy”. It is available in the App and Google Play stores.
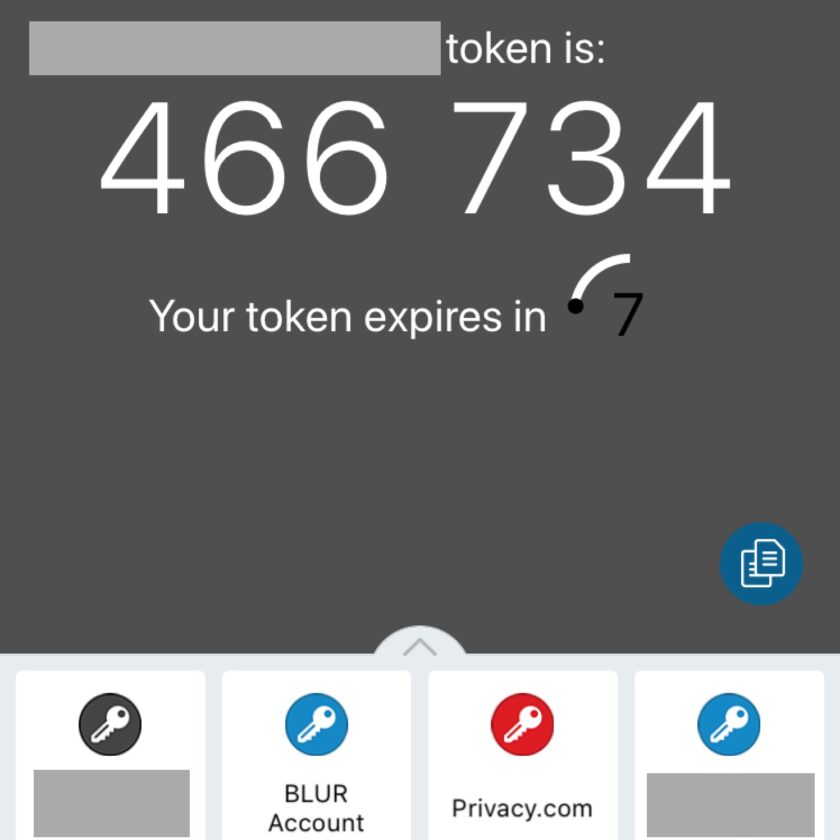
Here’s how it works (consult the website you are enabling 2FA for specific instructions): Install the application. Login to your account and find the security settings. Select “enable 2FA” (or similar) and choose verbiage that looks like an “authenticator app” or “Google authenticator”. You will then open your app and scan a QR code. The QR code transmits a token to your device. In the future when you log in to that account you enter your username and password, then consult the app for a six-digit 2FA code (the code changes every 30 seconds).
Footnotes
*OK, so let’s talk about the OPM hack. Really this is applicable to any hack or breach or spill, but let’s just use OPM as an easy example. Sure, your stuff has been hacked by them, and that sucks. But that doesn’t mean your SF86, fingerprint card, etc., etc., is for sale on the open market. That means a state actor has it. Fortunately, they are probably protecting it better than USG is protecting it even now. That data is a massive intelligence haul for whatever entity got it; they aren’t going to sell it to low-lives who want to commit employment insurance fraud in your name, and certainly aren’t going to give it away. So yes, OPM got hacked, but think about what that actually means before going down the submitting to Security Nihilism.
Actually, the fact that OPM got hacked means you probably need more security, not less. A state actor committed that hack for intelligence value. You’re not much more likely to be elicited…or further exploited digitally if you are assessed to be of some intelligence value.
**A dictionary attack is a pre-defined list of words that an attacker will test in an attempt to find your password. There are a number of ways an attacker might choose a dictionary.
- The least focused way an attacker might get a dictionary is by downloading a really generic one. These have a high probability of success in cases where “any account will do,” i.e. the attacker wants to get into any email account to harvest it’s contact list to serve email spam. With a list of the 1,000,000 most common passwords (compiled from the results of previous password breaches), an attacker will get into someone’s account with this method.
- There are also regional, language, and cultural-specific dictionaries. These are slightly more focused, and probably have a slightly better chance of success against a specific individual.
- If someone is attempting to gain access to your account specifically he or she may well almost certainly craft a custom dictionary. There are applications (search “Common User Passwords Profiler”) that allow you to quickly and easily build a custom dictionary against anyone. You simply open the application and fill as many fields about the person as you know. Names (their name, the names of their spouse, children, parents, etc.), significant dates, phone numbers, etc. The application will generate a list of millions of possible passwords that are designed around that individual’s personal information and heuristics of how humans make passwords. For example, the most common way to obfuscate a password is to add a number (or numbers) to the end of a simple, dictionary word. If I know that, and that your name is “Chris” and that your birthday is in June, I would certainly try combinations like “chris6”, “chris06”, etc. Though this seems really, really simplistic, it’s not when millions of combinations are produced and can be tested. Humans are terribly unpredictable.