In the last three parts of my Digital Security Primer I discussed the importance of digital security, making your device a hard target for malware, and protecting your cloud-stored data. This time I am going to get into the cool, sexy stuff: encryption for your data-in-motion. But first, I’m going to make some of you angry.
Intro Rant
I’ll cut to the chase: the gun-related stuff is by far the most popular stuff I publish. I assume I have a strong contingent of followers who are interested in guns. If you care about your gun rights and believe a national gun registry is a bad thing, you’ve got to do more than sitting around bitching about people with a different symbol beside their name than the symbol beside your name. Part of what you can do is begin limiting the data you hand over to a government who is hostile to your gun rights. Saying, “if the government wants it they’ll find it” is hypocritical, intellectually lazy, and designed to absolve the speaker of taking any action. Your rights won’t protect themselves; protecting them is OUR responsibility.
This post is super timely. Right now – while everyone is distracted with COVID-19, Congress is trying to pass the “EARN IT” Act, which would make it possible for the government to ban strong, effective encryption. I want the government to be able to catch criminals as much as the next guy, but this greatly increases the already tremendous imbalance of power between the government and The People. Paying attention to this is probably more important than reading yet another comparison between the P365 and the Hellcat.
Basic Flow of Data
Let’s begin by talking about how your data moves and how it gets attacked. When you power up your computer open your browser, connect to the internet, and click that button for your favorite site, you kick off a chain of events. Your traffic is broken down into packets. Packets are small, manageable chunks of data that are reassembled into their whole once they’ve gone down the pipe of your internet connection and arrived at their destination. These packets are routed through several different pieces of hardware.
As the illustration below demonstrates, there are four basic categories of hardware your packets touch: your computer (1), your internet access point (2), servers, trunks, fiber, and other hardware owned by ISPs (3), and finally, the destination website. There are different vulnerabilities across all of this hardware. Let’s address them in order.
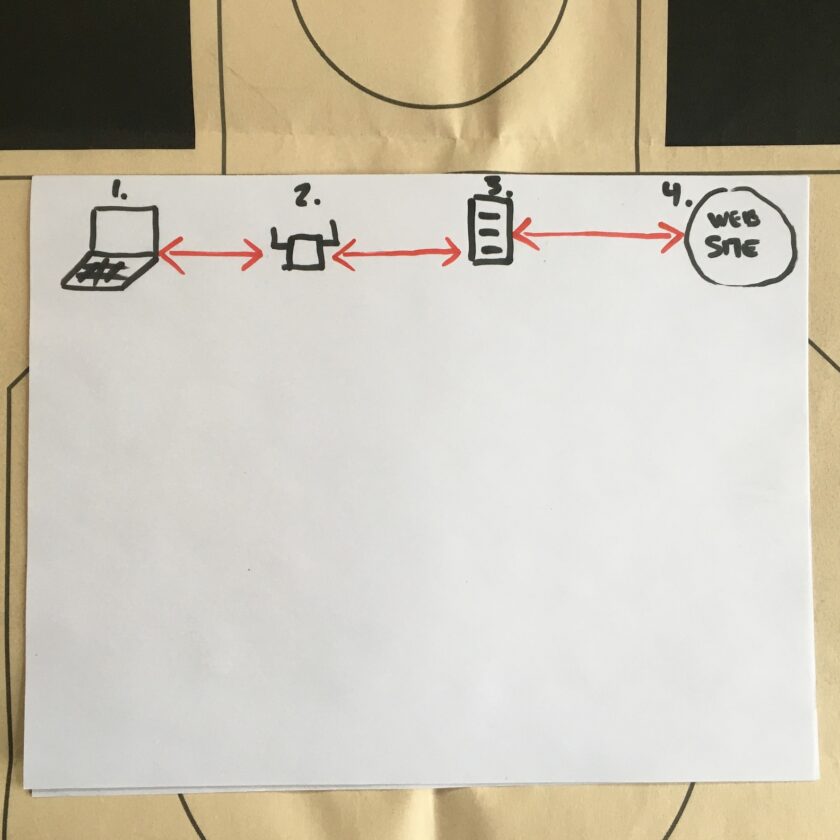
The first is your computer, where the data originates. If your computer has malware, it doesn’t matter what high-speed, low-drag encryption you put on the actual traffic. The bad guy can read your stuff directly off of your keyboard. I discussed this, and how to harden your device against malware – in part 2 of this primer. Your access point (AP) probably consists of your wireless router and your modem. Nowadays you probably rent both of these from your internet service provider. The next touchpoint is your internet service provider (ISP), who routes your traffic to the website you wish to visit, and returns the appropriate results. Keep in mind, my diagram is greatly oversimplified, but it still serves the purpose.
Threats to Data
That is roughly how your data flows. The threats begin as soon as data is put into motion. When data leaves your computer to the access point it is vulnerable. I will discuss how to mitigate all of these threats further down.
The first red line – between the computer and the access point – is the first major vulnerability. If you are on Wi-Fi a radio signal moves your data between these two points. Anyone with an appropriate radio can “listen in” on these signals. There is a free operating system called Kali Linux that is – quite literally – purpose-built for hacking Wi-Fi. Extended-range Wi-Fi antennas are cheap and freely available on Amazon and enable monitoring Wi-Fi traffic from longer distances. If you have a computer, $50, and some hours to spend on YouTube, you, too can begin collecting Wi-Fi packets. If you want to spend a few more bucks your attacks can get massively more sophisticated.
Often these packets are encrypted. If you had to provide a password to gain access to the router, they probably are. But if you connected to a public network, like a hotel, they almost certainly are not. Don’t be fooled by the requirement to enter your name and room number when you login at a hotel. Hotel networks are almost universally unencrypted, and a huge honeypot for bad actors.
From the router, your traffic goes to the internet service provider (the second red line). Here the traffic is much more difficult for an average Joe to exploit. Unfortunately, it’s really, really easy for the internet service provider to exploit. And they do. In April of 2017 President Trump repealed rules that prohibited ISPs from collecting and selling data on all your internet activities. Your ISP can literally catalog every single site you visit, how long you spend at each, and where you go from each.
Think about it; your ISP knows if you’re into guns, prepping, the King James Version Bible, and anime erotica. They also know if you’re more of a ARFcom / recreational weed / Grindr kind of guy. Your ISP knows if you’re cheating on your wife and probably, with whom. Do you really trust them with all this information? (Before you get mad I strongly recommend reading A Billion Wicked Thoughts. Those people are out there. You know it. I know it.) Just think about what the list of websites you visit says about you and how that information could be misused. If it doesn’t alarm you, it should. Fortunately, we can fix a LOT of this with some simple, top-down mitigations.
HTTPS
The first is the simplest of all: HTTPS. HTTPS stands for something that isn’t really relevant, besides the “s”: SECURE. We are usually oblivious to HTTPS connections because they are so ubiquitous (literally; HTTPS is the most ubiquitous form of encryption in the world). But what does it mean?
An HTTPS connection means a couple things. First, it means the site you are visiting has purchased an HTTPS certificate. The certificate contains some information that is shared with your browser. The site and your browser establish a “handshake” and share some encryption keys. Once this happens (usually in the blink of an eye) everything you share between your computer and the site is strongly encrypted.
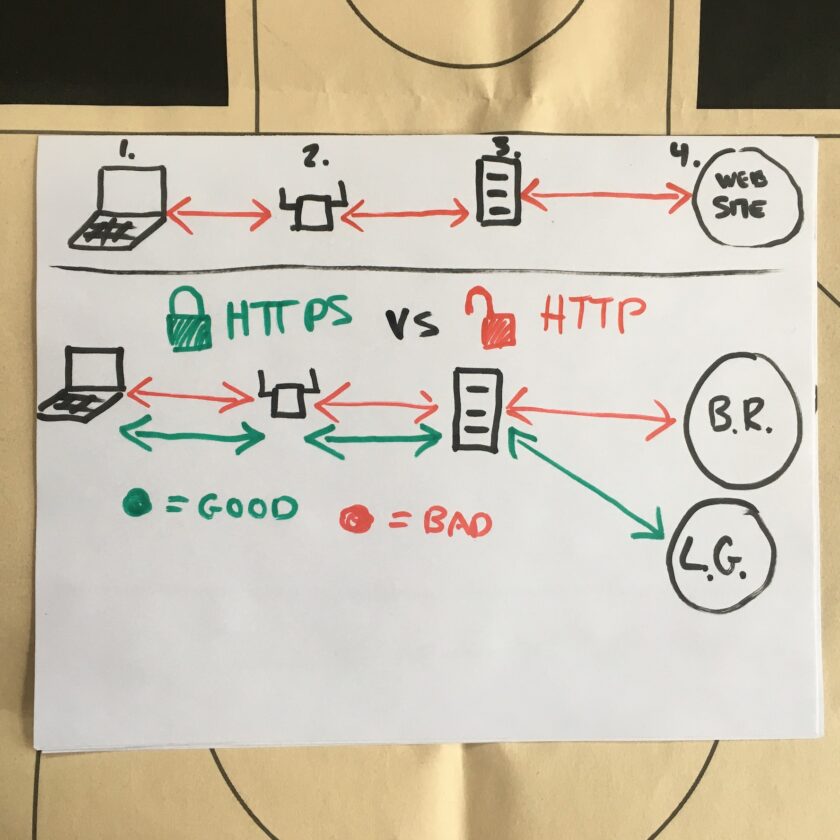
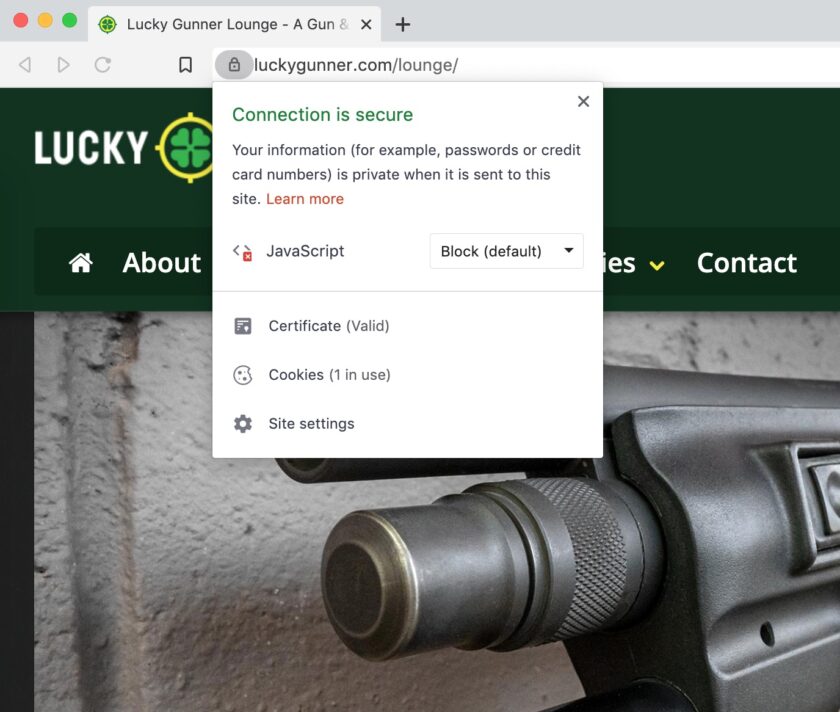
This accomplishes a LOT. The diagram above shows a HTTPS website in green, and a website that does not offer this protection in red. For uniformity’s sake, I will use the same two sites: LuckyGunner.com (secure, HTTPS) and BallisticRadio.com† (insecure, non-HTTPS) throughout this article. Look at the green line; your data is protected from the moment it leaves your computer until it gets the destination website. Even better news: you have to do basically nothing to get this protection! If the site has HTTPS, you probably get the benefit of it.
This system is not perfect, though! First, it relies on sites to comply. Sites must purchase and install an HTTPS Certificate. This is not terribly onerous; I am a self-financed, single-man operation with very, very minimal revenue. Still, I manage to come up with $60 or so per year to provide my readers with an HTTPS connection. This is not unique to me and I’m not patting myself on the back; something like 90% of sites on the internet are now HTTPS sites. If a site cannot afford an HTTPS certificate, they can request one completely for free through the non-profit Let’s Encrypt.
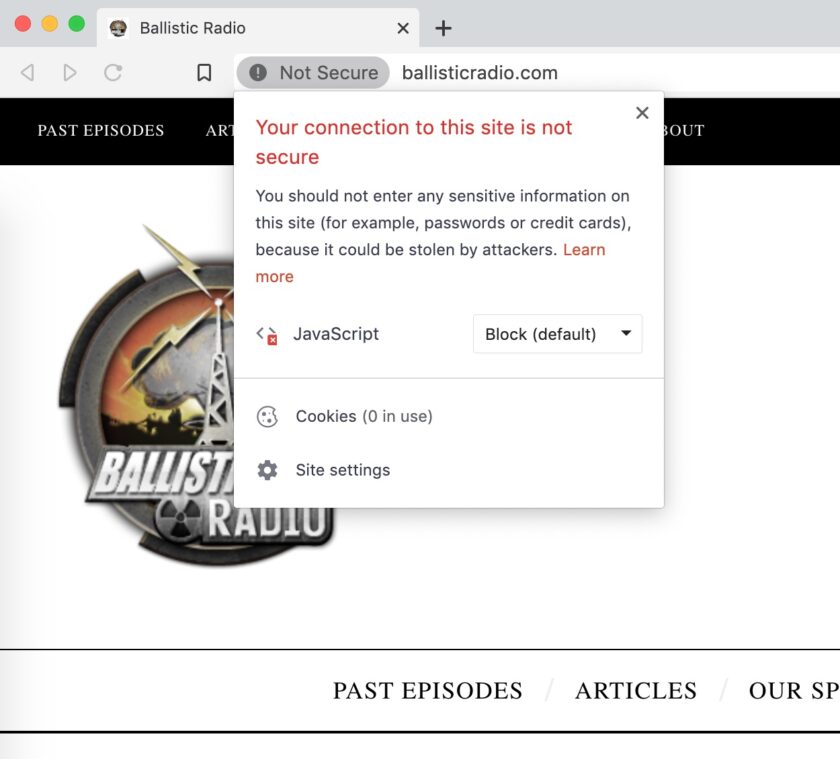
Another problem with relying solely on HTTPS is that it does not protect everything. Interested parties between you and the destination website don’t get to see what you do on the site (what pages you view, what information you input, etc.), but they do get to see you’re on that page. If you visit luckygunner.com your ISP can’t see that you’re looking at 9mm and 5.56 ammo, but they do know you’re visiting an online ammo store. They can’t see any entered passwords, search terms, the exact pages you are visiting, etc. because all of this is encrypted. But, the list of sites you visit still gives a LOT of information up about you and your interests, habits, etc.
Finally, HTTPS does nothing to protect you from the site you are visiting! If you visit “sketchyrussiansite.ru” you shouldn’t trust it just because there is a green padlock in your address bar. Sure, your connection to that site is secure…but that’s kind of like driving an armored car right into the bank robber’s lair and unlocking the doors.
How to Use HTTPS
As I mentioned earlier, it’s mostly on the site to provide it. I have had extremely good luck in simply informing the websites that I enjoy that I appreciate HTTPS-encryption. I point out that 90-something percent of the ‘net is encrypted, and that certificates are available for free. Occasionally I get ignored, but user demand is a real thing, and I have gotten several sites to install HTTPS certificates simply by asking.
If you really want to increase the number of HTTPS-encrypted connections, install the HTTPS Everywhere add-on on your browser. This is a simple modification that does not require ongoing effort, and actually makes a meaningful change. I will write a separate article about this in the near future. One of the huge benefits of HTTPS Everywhere is that by enabling the “Encrypt All Sites Eligible” you get a huge warning when visiting a non-HTTPS-encrypted site.
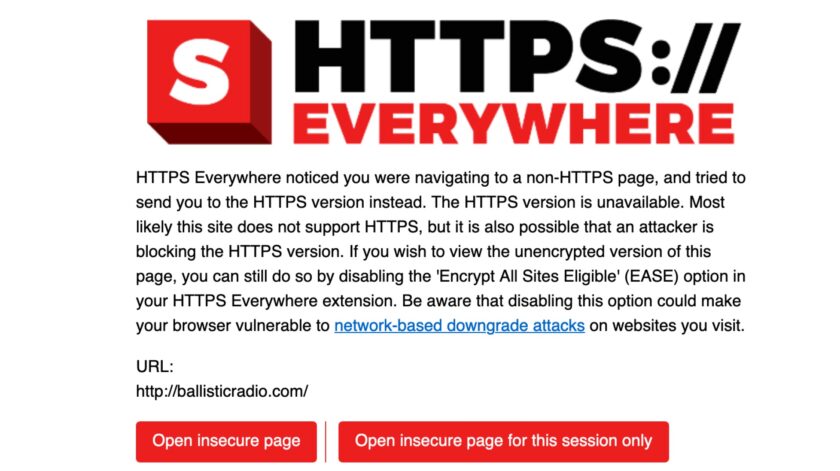
Virtual Private Networks
The next layer of protection over your data in motion is a Virtual Private Network (VPN). Sounds intimidating and complicated, but it’s not. Let’s take a look at the next diagram.
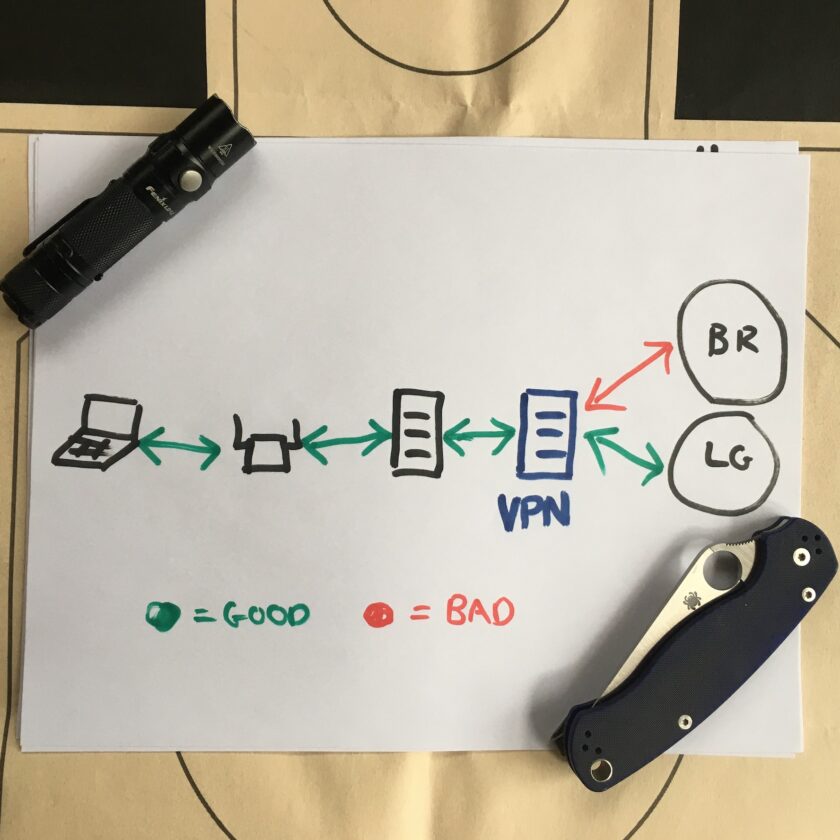
A VPN is a massive upgrade over HTTPS…or nothing. Using a VPN requires subscribing to a service and installing an app on your device. The services gives you access to the VPN’s network of servers and bandwidth. The app encrypts all your traffic, then routes it to a VPN server before sending it to the destination website. Available servers depend on the exact VPN service you purchase.
This does several things. First, it prevents the ISP from even seeing what sites you visit. Because all my traffic is encrypted to the VPN server, my internet service provider doesn’t know if I’m streaming Netflix, watching porn, or doing a video chat with my family. All the ISP can see is a line of communication between me and the VPN server.
Best of all this is a PROACTIVE measure; no longer am I relying on the sites I visit to protect me, I’m choosing to protect myself. If I’m on a hotel network everyone from the kid in the parking lot to the hotel’s own hardware to the internet service providers handling my data see nothing except a connection between a user and a VPN server.
Virtual Private Networks also protect you in another way. They make it really difficult for websites to see your I.P. address. Your I.P. address is the numerical address on each of your packets. This address is like a street address; it’s how the internet knows how to get the site you request back to you. Here is why that is important: your I.P. is directly linked to your subscriber account with your ISP. This allows data collection systems to very closely correlate certain internet activity with YOU specifically.
IMPORTANT NOTE: A VPN WILL NOT MAKE YOU ANONYMOUS! Being anonymous is a lot like being pregnant: it’s awful hard to be a little anonymous. Anonymity requires a lot more than a $4/month application. What a VPN gives you is a strong layer of privacy.
How to Use a VPN
Using a VPN is pretty easy but can present some special challenges. One of the biggest is simply selecting a VPN. The industry is rife with affiliate programs that reward resellers for peddling certain VPNs. VPNs inflate their own effectiveness, touting “anonymity” and such. Instead of marketing I would look for the following:
- Do they support all my devices? A good VPN should support your computer, table, and phone, and those of your family members. “Support” also means having servers in favorable locations, allowing a sufficient number of device connections, and
- Do they have a strong privacy/logging policy? VPNs have access to all your traffic. You want to take great pains to choose one that handles this data responsibly.
- Do they offer strong security protocols? I will explain this stuff in the future (maybe) but the encryption should be AES-128 (minimum) or AES-256 (preferred). The key exchange should be RSA-2048 (minimum) or RSA-4096 (preferred). The handshake protocol/SHA should be SHA-256.
- Do they use accepted best practices? Do they do first-party DNS lookups, block IPV6 requests, and offer the OpenVPN protocol? Are they anticipating a full release of Wireguard and planning to implement it?
If that sounds confusing, I get it. I try to shy away from making specific recommendations these days because things change so quickly, but I have no problem telling you what commercial VPN I use: ProtonVPN. I have no financial relationship whatsoever with ProtonVPN, other than paying full price, out of pocket, for my own account
Once you’ve selected a VPN and paid for it, you will have to download the application and install it. Most are fairly self-explanatory: you choose a server location (i.e. “US – Salt Lake City”). This is the server you will appear to be from to the websites you visit. Beyond that it is simply a matter of using it. I have ProtonVPN configured to startup immediately on booting my computer. I have the phone app configured to always keep an active connection .
Closing Thoughts
This article is broken into two parts. The next half of Part IV will cover encrypted messengers. I think those products are critically important and will discuss them, in detail. These are the low-hanging fruit steps you can take to give you a very strong layer of protection against a wide array of adversaries. Spend a few bucks on a VPN, install HTTPS Everywhere, and if you run across a site not using HTTPS, let ’em know it matters to you.
†In fairness to BallisticRadio.com, I reached out for comment several times prior to writing this article and never received a response of any kind.





1 thought on “Digital Security Primer Part IV.I: Data In Motion”
Comments are closed.