I have been using ProtonMail full-time for over five years, and recommending it for almost six. My contact form forward emails to a ProtonMail account, and any of you that have interacted with me have done so through ProtonMail on my end. A lot has changed since ProtonMail’s beginnings. This post will cover the basics of ProtonMail: how it encrypts your data-in-motion, data-at-rest, and some other features.
In the last installment, we discussed differences between the various paid tiers and the paid features available with each. Today I’m going to dig into the nitty-gritty of the user-configurable security features included in ProtonMail. Though ProtonMail is meant to be out-of-the-box secure, the user can improve upon the security of the stock configuration. Some of these features are quite complex, so bear with me.
Full Disclosure
Obviously I am a fan of ProtonMail, and I selfishly want others to use it so more of my communications are encrypted. However, I have pay full price – minus discounts available to all ProtonMail users – for both of my paid ProtonMail accounts (one a ProtonMail Plus plan, one a ProtonMail Professional plan). I pay full price, out-of-pocket and have received no discounts, free service, or any other incentive from ProtonMail.
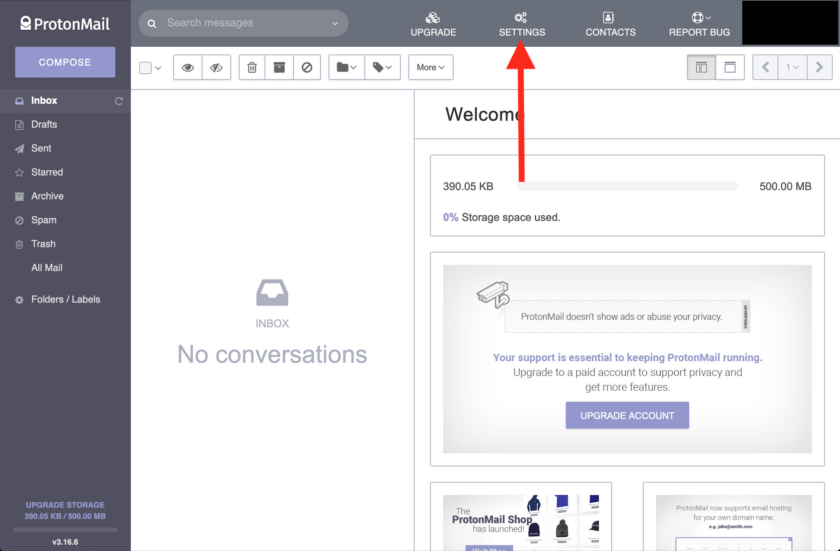
Most of the features discussed in this post are available to all ProtonMail users, including the free tier. Accessing them requires first logging into your account, then clicking the “Settings” button along the upper banner.
Email Content
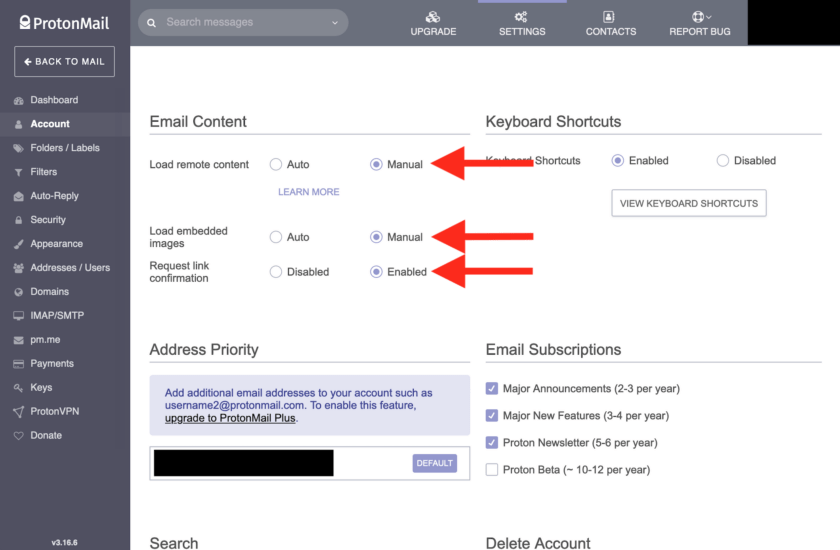
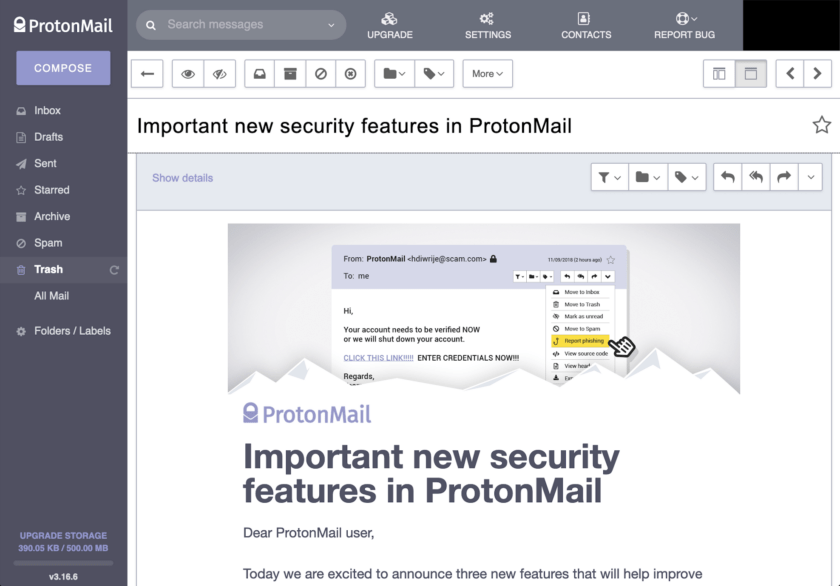
This is a very important and often overlooked set of security/privacy settings. These settings can allow you to prevent media and images contained in emails from automatically loading. Unfortunately this makes many automated emails look “broken” but for good reason: none of the images and content can load.
If images are allowed to load, “tracking pixels” can also load. These are small (1 pixel x 1 pixel) “images” that designed to be invisible to the user, but that connect to a remote host to share information about the user. Preventing these from loading can cut down on a lot of information that is collected through email marketing. If you’d like to know more, consider reading this excellent explanation of tracking pixels.
I strongly recommend that both “Load Remote Content” and “Load Embedded Images” be set to Manual. To access these settings, click on the “Settings” button on the top banner. Next, ensure you are in the “Account” tab from the menu along the left side of the screen.
When you receive an email that contains remote content or embedded images, you can load them by clicking the “Load” button at the top of the message.
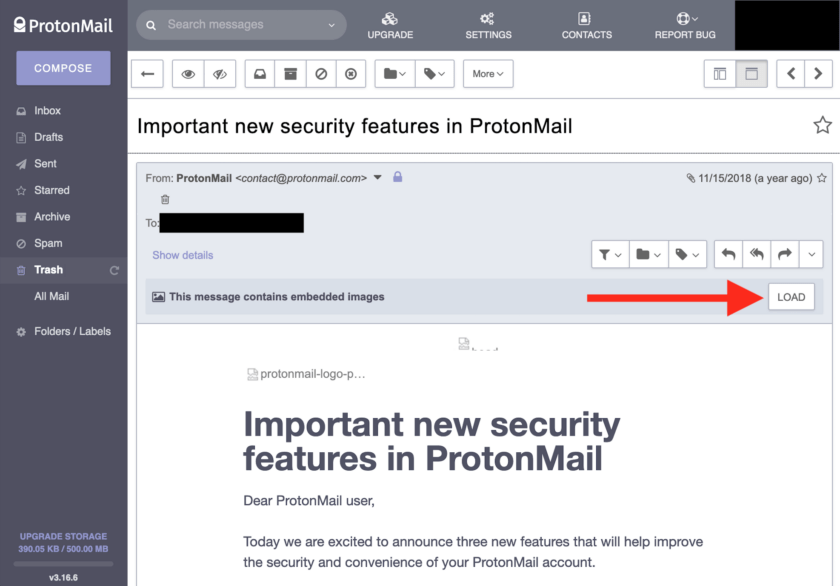
This gives the user the choice to load emails that she trusts, while excluding all others. It is very rare that I find the need to permit images from an email to load.
The third setting in the Email Content set of settings is “Request Link Confirmation”. I recommend enabling Request Link Confirmation. It improves your security in two ways. First, it asks you to confirm that you wish to visit any link that you click. This is a good layer of protection against accidentally clicking a link. Secondly, it shows you the entire link, which you otherwise may not see if the link is embedded in text, buttons, or images.
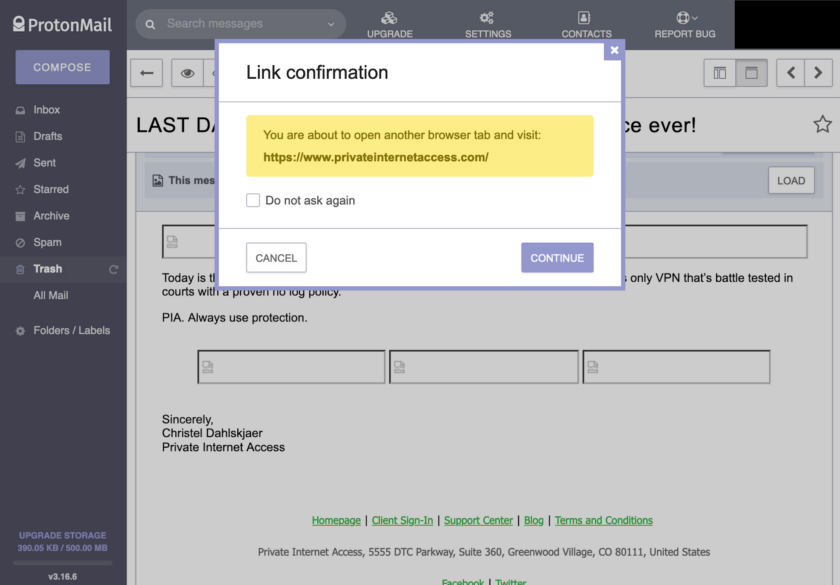
All of these settings make ProtonMail slightly less convenient to use, but only slightly. This very minor decrease in convenience comes with a out-sized increase in security. Again, I recommend all of locking all of these settings down.
Password Settings
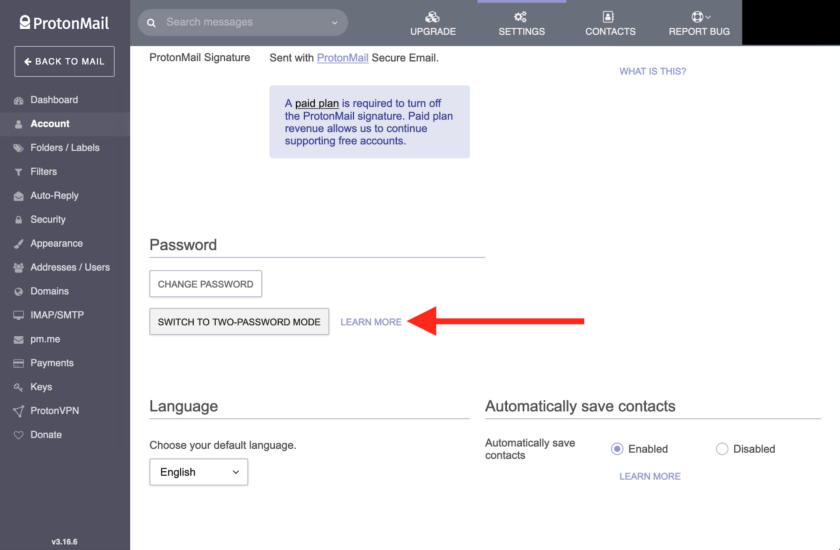
The next set of settings deals with passwords. The first lets you change your password. If your password isn’t great, use this opportunity to fix it! The next setting allows you to enable ProtonMail’s once-famous and mandatory (and now likely forgotten) “Two-Password Mode”.
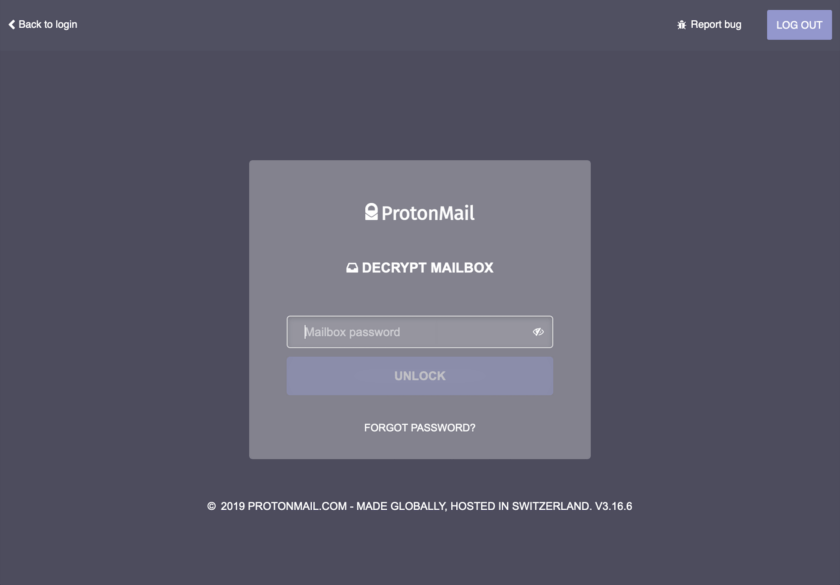
Two-Password Mode allows the user to require two passwords for access to the account. The first password logs the user into his or her account and proves ownership of the account. With one password alone you still can’t access the contents of the account, however. The second password decrypts the user’s mailbox. The word “mailbox” is a bit misleading in this context, as it includes not only emails, but also login event logs (discussed further down) and the user’s secure contacts.
Personally, I like the legacy two-password mode, but I understand why others wouldn’t. Two-password mode is more secure, though only slightly so, than single-password mode. For absolute security, I recommend using it, but the single-password mode is generally “good enough”. One other thought: if you only use ProtonMail on an app (be it a mobile app or in Thunderbird via Bridge) you only have to login once, so why not make it two-password mode?
Two-Factor Authentication
ProtonMail offers good front-end security, aside from Two-Password Mode. The first of these is two-factor authentication. ProtonMail’s two-factor authentication scheme utilizes the Time-Based, One Time Password (TOTP) protocol, which requires a mobile app and a specialized app (I recommend Authy). Step-by-step instructions for setting up two-factor are available from ProtonMail here.
Once two-factor authentication is setup, you will have to enter you username and password, followed by a six-digit code that you retrieve from the app on your phone.
I strongly recommend you enable two-factor authentication on your ProtonMail account. Keep in mind that this is not the same as Two-Password Mode. Also keep in mind that Two-Password Mode is not a replacement for two-factor authentication! Two factor is important because it protects you from keyloggers and other types of attacks that could capture your password. Many of these methodologies would still leave your second authentication untouched.
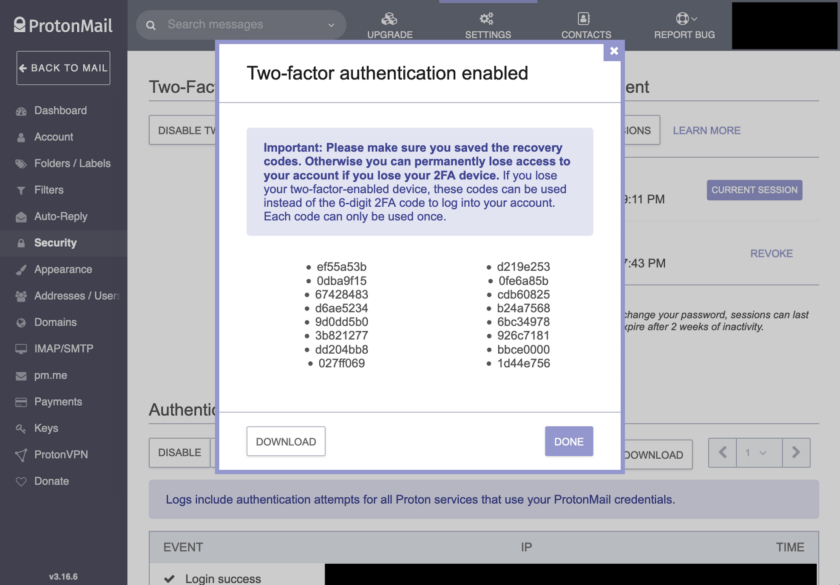
If you set up two-factor, there is some risk that you will lose your phone, which could result in losing access to your ProtonMail account. To protect you from this, ProtonMail provides a set of 16 backup codes. These eight-digit, alphanumeric codes can be used instead of a code retrieved from your phone. I recommend saving these and storing them in a secure location. I typically copy them as text and place them in the Notes section of my password manager entry.
Authentication Logs
ProtonMail’s authentication logs allow you to monitor login events. You are allowed to choose either “basic” or “advanced” logging. The difference is that with “advanced” logs you are provided an IP address, in addition to the description of the event and time stamp provided by the basic log. These event logs are stored inside your mailbox and encrypted with your private key. As such, they are accessible only to you.
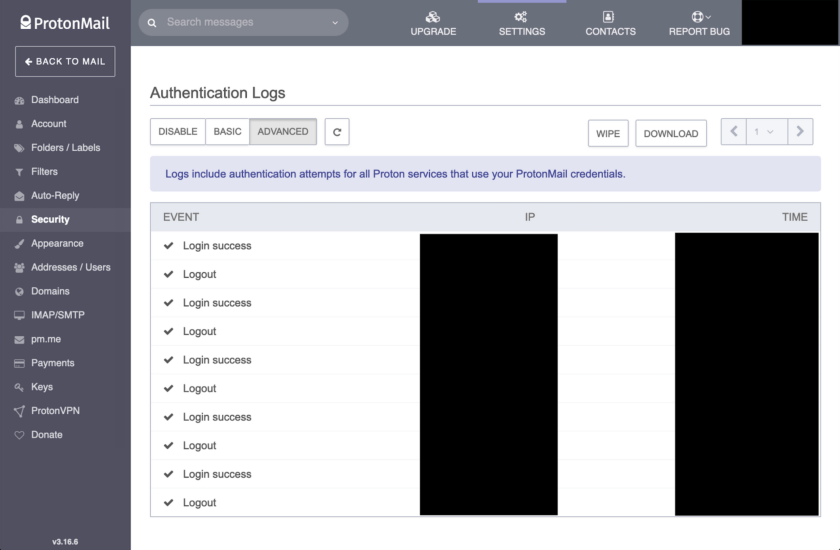
My take on event logs is use the basic event logs. Having the IP address is nice, but let’s be honest – most of us aren’t going to recognize the IP address anyway. If you’re using a VPN (and if you’re reading this blog there’s a very good chance you do) that IP is going to be changing constantly. If you’re not using a VPN you have a much better chance of recognizing the IP, but your priority should be choosing, purchasing, and using a VPN.
Key Management
Finally, we get to the really good stuff: key management. By default, ProtonMail generates a RSA-2048 key when you create your account. If you upgrade to paid account, you get to choose your key strength for future addresses, but that first one is always 2048. Unless you change it. ProtonMail allows you to change the primary key for each address and generate multiple keys for a given address. You can also delete old/unused keys but be careful; you will not longer be able to access emails encrypted with them.
To generate a new key, click on the “Keys” tab on the left-hand menu bar. Click on the “Add New Key” button. This will open a dialogue asking which address you’d like to associate the key with. If you are trying to upgrade ALL your contacts to RSA-4096 or ECC, you will have to repeat this entire process for every address you have.
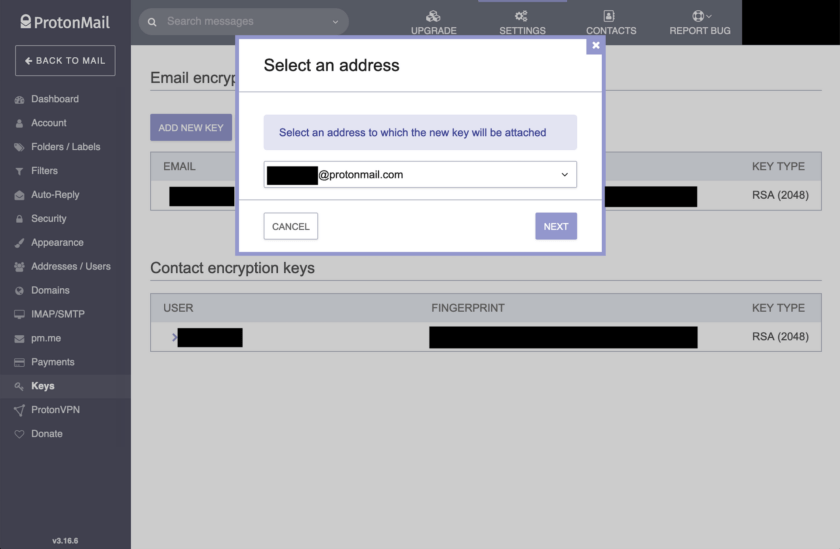
In my example I am using a free account, so I only have one address available. Next, choose the strength of the key. Default is RSA-2048 which is generally considered to be secure. I much prefer RSA-4096 for future-proofing, and lately I have been experimenting with the Elliptic Curve Cryptography (ECC) algorithm (X25519). The ECC keys are incredibly short, and as a result fast. They are also probably stronger than RSA keys, but haven’t undergone the same level of vetting.
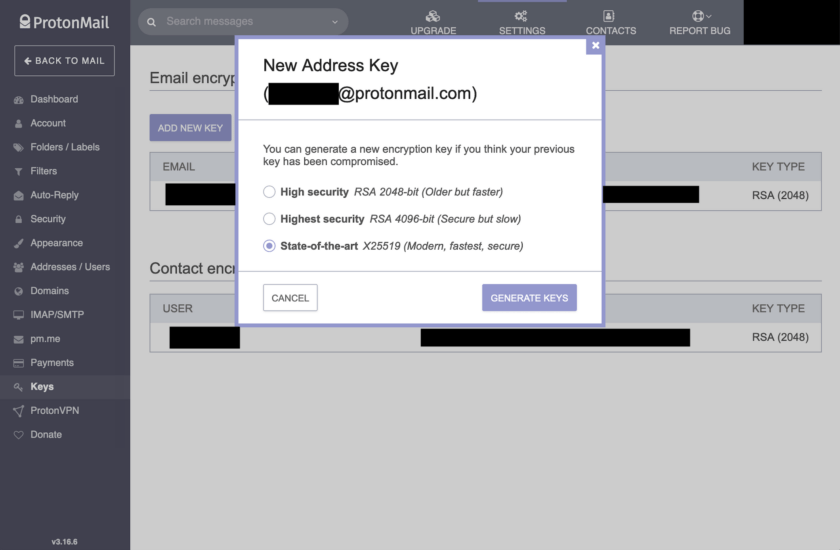
Once your key has been generated it is automatically assigned to the address you chose earlier. For it to be used, you have to assign it as the primary key.
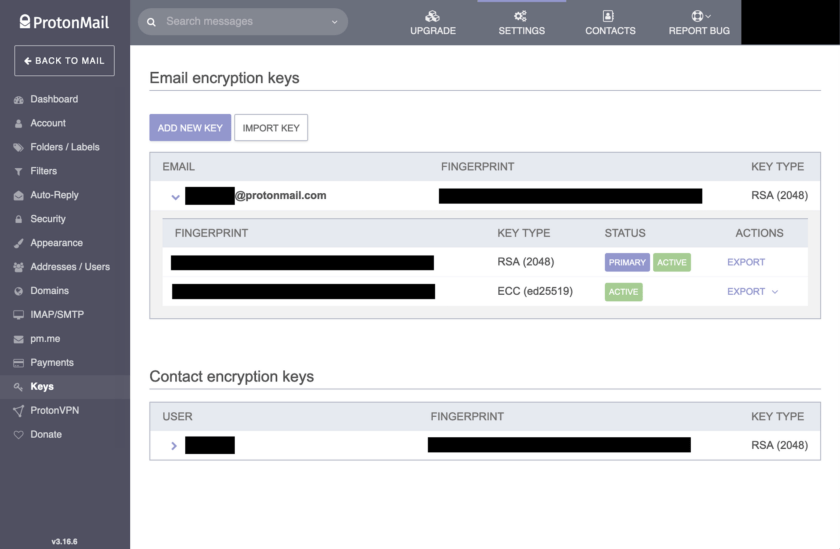
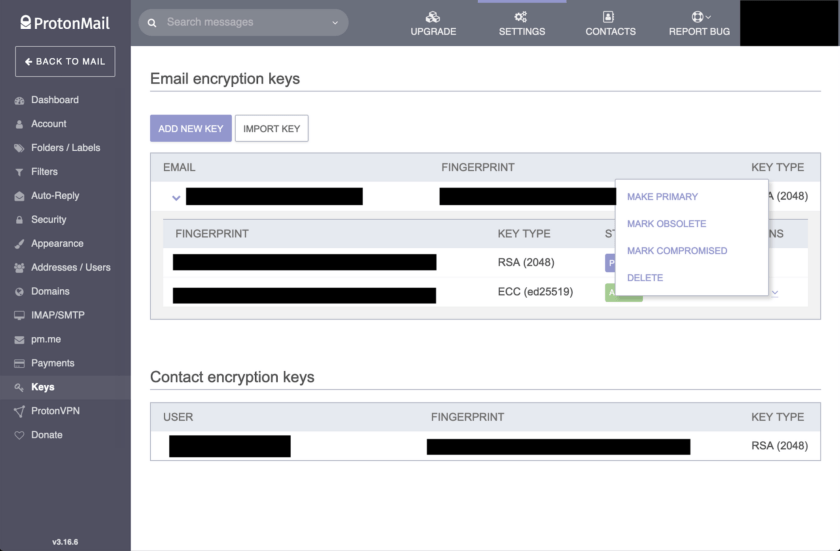
To do so click on the arrow beside “Export” on the new key. Several options will appear. Choose “Make Primary”. This new key will be used for encryption now. If you want to ensure that your old key can no longer be used, you can mark it as obsolete; messages will now longer be encrypted with it. You can also delete keys, but again, an abundance of caution is advised here because you will lose access to any emails encrypted with those keys.
PGP Integration
ProtonMail also lets you integrate with people who are still using old-school, manual (and more secure) PGP. I used this implementation of PGP for a long time, but don’t any longer and I don’t recommend it unless you have serious security concerns. Some people do have serious security concerns, though. Glenn Greenwald is one of them; I used him and his public PGP key as an example in the following screenshots. Because his email address is protected on his site, I did not use his real email address, however.
The following will assume that you are somewhat familiar with PGP-encrypted email. If you are not I have written a lot about it on this blog; you can teach yourself how to use it using those articles. . To add someone’s public PGP key, add that person to your contacts.
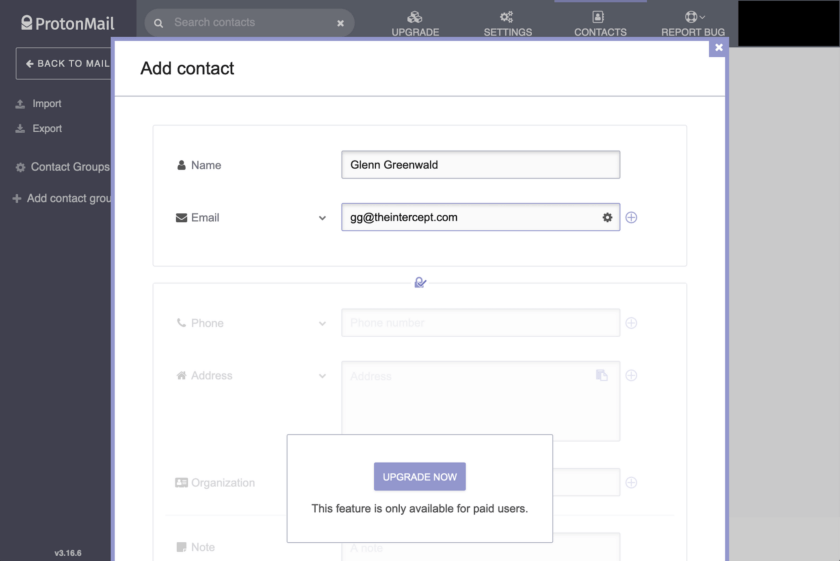
Next, save that contact, and reopen it. A gear-shaped settings icon will appear that will allow you to access Advanced Settings.
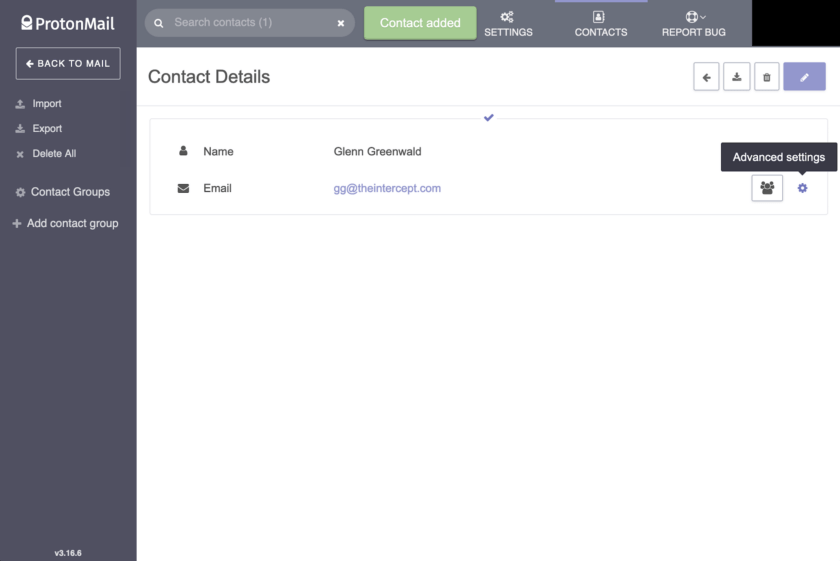
Within the advanced settings an option is available to “upload key”. Obviously this requires having access to the other party’s key, and I assume if you’re doing manual PGP, you know how to get a key.
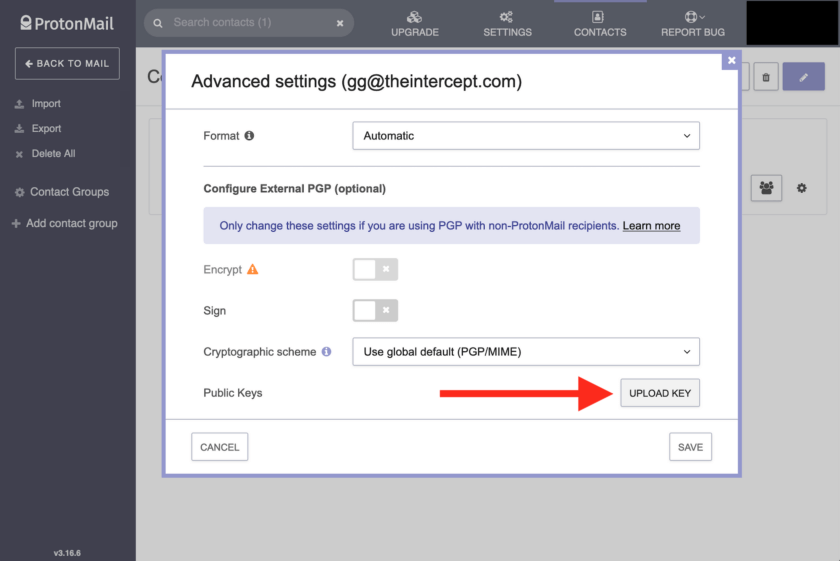
Once a key has been uploaded you now have the ability to automatically encrypt and/or sign messages to the recipient. I am incredibly pleased with the ease of use of this system.
Sharing your own public key is also fairly simple. Under the “Security” settings tab is a block labeled “External PGP Settings (Optional)”. From this menu you may enable message signing and “Automatically attach public key”. This will attach your key to all messages you send; personally I don’t attach my key, and the number of people who have asked me to share a key is zero…but that’s up to you.
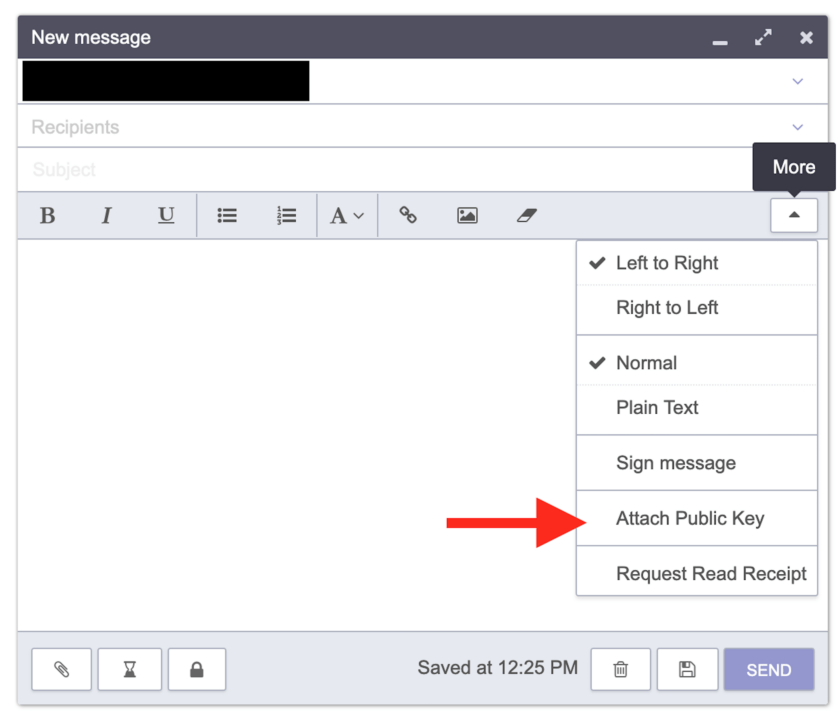
Keys can also be attached to messages individually. In the compose pane, click the “More” button. One of the options here is “Attach Public Key”.
In Summary
Today we covered most of ProtonMail’s considerable security features. In the next (and final) installment of this series, I will address ProtonMail’s “Address Verification” system. Address verification is a scheme used to verify contacts, and one of ProtonMail’s most poorly integrated and poorly documented features (in my opinion). Stay tuned.