I have been using ProtonMail full-time for over five years, and recommending it for almost six. My contact form forward emails to a ProtonMail account, and any of you that have interacted with me have done so through ProtonMail on my end. A lot has changed since ProtonMail’s beginnings. This post will cover the basics of ProtonMail: how it encrypts your data-in-motion, data-at-rest, and some other features.
VMs Part 1: Creating Your First Virtual Machine
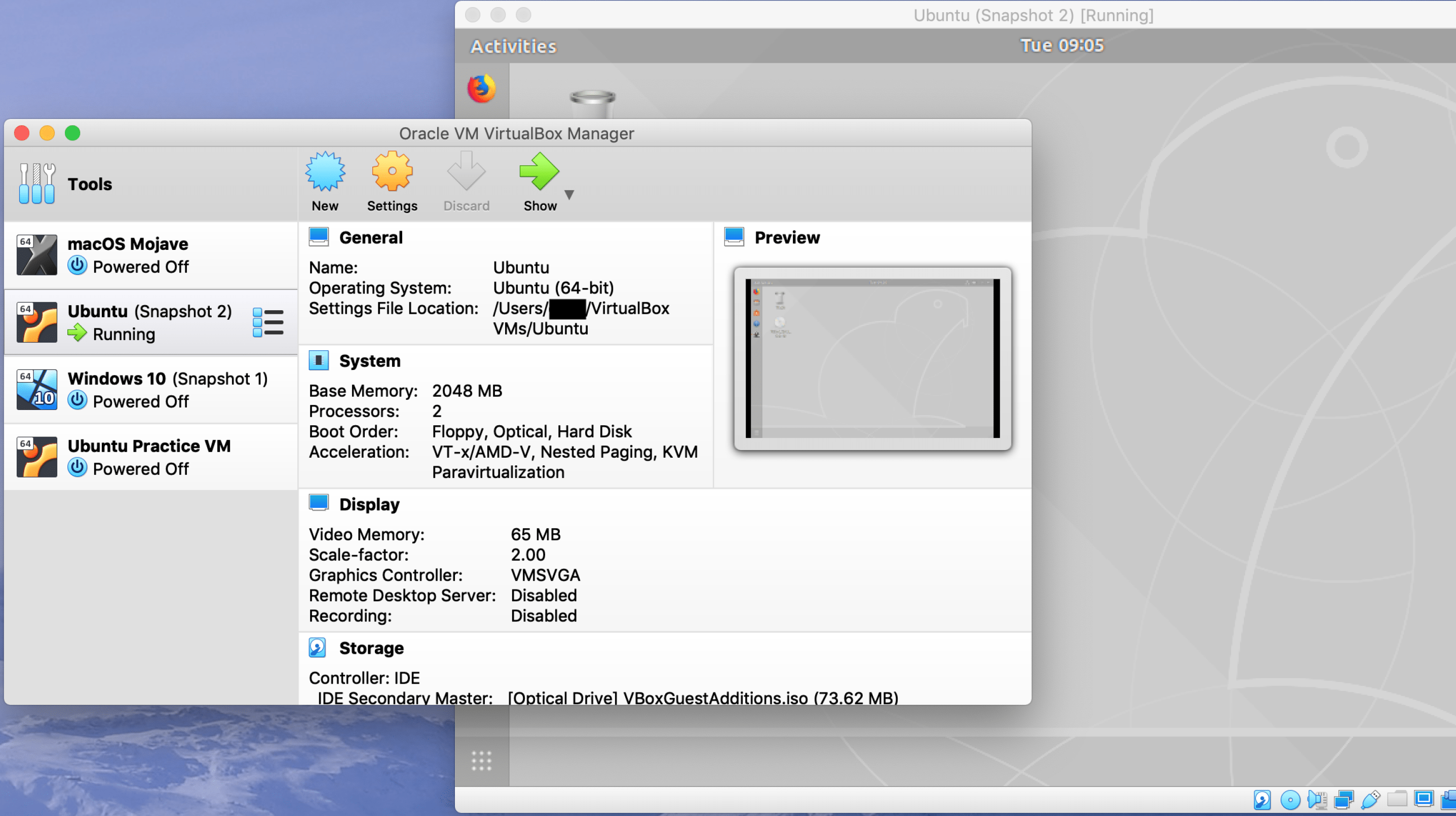
It recently occurred to me that in over five years of running this blog, I’ve never given step-by-step instructions for setting up or using a virtual machine (VM). It is likely that a lot of you already use VMs don’t need a tutorial. If that applies to you, please share this with a friend who does. It is equally likely that some of you could use step-by-step instructions. This tutorial will cover creating your first virtual machine.
The Apricorn Aegis SecureKey Flash Drive
The Apricorn Aegis family of flash drives, HDDs, and SSDs has been around for quite a while. I’ve generally rejected them based on price alone. Recently a customer requested training that included this drive. Since learning the Aegis and its capability, I’m very impressed. If you have compelling data security needs, this product might be for you.