This post will examine and explain the Mul-T-Lock high security lock. Besides the Medeco, this is one of the most popular high-security locks on the US market. If you live in a major metropolitan area in North American, you probably walk by these on a daily basis. If you’re looking to improve the lock on your home, you could do a lot worse than one of these.
Recognizing the Mul-T-Lock High Security Lock
The Mul-T-Lock high security lock is extremely distinctive for two reasons. First, the keyway looks like few other keyways. It is rectangular without the curvature of most standard pin-tumbler keyways. If mounted in a traditional orientation, the keyway also runs left to right instead of up and down. Secondly, the Mul-T-Lock logo is unmistakable. The photo below are Mul-T-Locks I encountered on Lock Safari NYC. Take a look at those keyways and the logo.


How the Mul-T-Lock Works
The Mul-T-Lock high security lock is known for its pin-in-pin design. This means that each pin is actually comprised of two parts: an outer pin and an inner pin. The key raises the outer pin to the correct height. The inner bottom pin may be the same length as the outer pin, or one cut depth longer or shorter. Below is a photo of a disassembled Mul-T-Lock.

What makes this lock difficult to defeat is aligning all of the outer pins at the shear line, along with all of the inner pins. Each cut in the key is really two cuts – one to raise the outer in, and one to raise the inner pin. The photo below demonstrates both the inner- and outer pins lifted to shear line. It is possible that all of the outer pins are raised to the correct height, but the inner pins are not. This results in the lock remaining closed, making this a very difficult lock to pick.
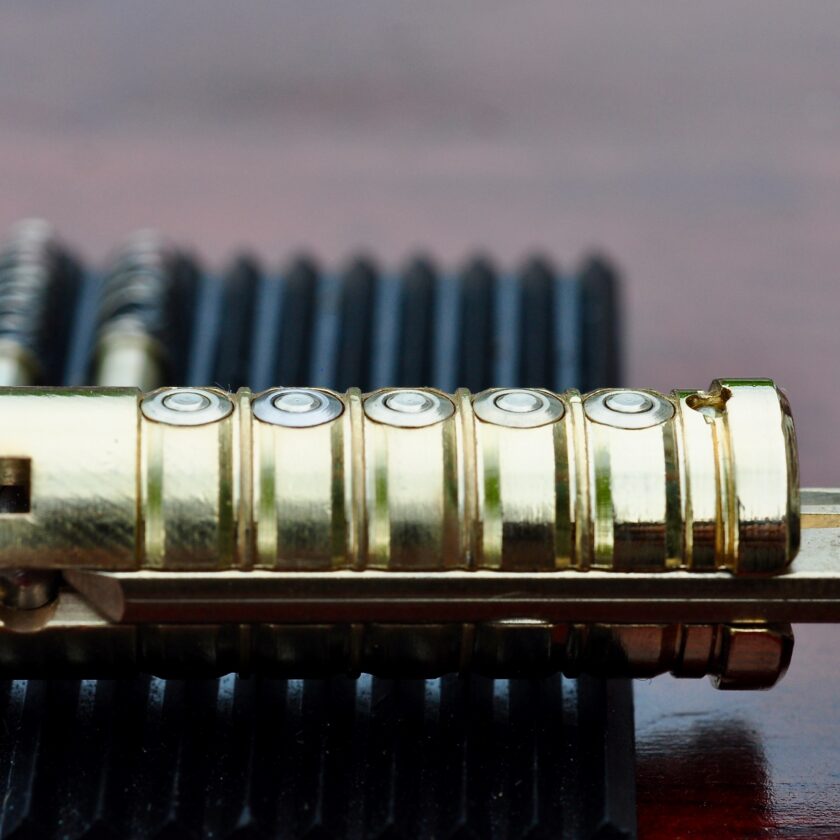
The Mul-T-Lock comes in three generations: the Classic, Interactive, and MT5+. The Classic is the most basic design, and the one seen here. The second-generation Interactive has a moveable element on the key, which makes the system much more secure.
This post was just a quick overview of the Mul-T-Lock. For more information check out Datagram’s whitepaper at http://lockpickingforensics.com/articles/mul_t_lock.pdf (INSECURE link).





