In my last post in this mini-series, I talked about Step 1 in my Security Framework: Malware Resilience. The steps there are all designed to minimize the chances of contracting malware. There are other steps, more advanced that can be taken, and maybe I’ll cover those in the future. They get much more technically demanding and time-consuming to implement.
Dry Practice Function Stacking: Targets
With a lot of you working from or otherwise hanging out at home, I hope a lot of my readers are using their time to learn some stuff. One thing I hope everyone stuck at home is doing is dry-practicing. Another thing that might nudge some into dry practice is the current ammo shortage. Today I’m going to talk about some very simple, low-cost things you can to do increase the value of your dry practice time.
Digital Security Primer Part II: Resist Malware
Malware is THE single biggest digital threat we face today.
Digital Security Primer, Part I: Why Bother?
As I mentioned a few weeks ago, I have recently written a book on digital security. This post is going to kick off a series on digital security (and secure communications – a skill that might become very important for freedom lovers in the near future) that roughly follows the outline of the book. This is completely free information that I make a very good living teaching. I’ve worked hard to put this into plain language (and perhaps even made it enjoyable to read, as well). If you enjoy this content, please consider picking up a copy of Digital Self Defense: The Layman’s Guide to Digital Security when it comes out this spring. Thanks!
Uncensored Tactical Podcast Appearance
I recently appeared on the Uncensored Tactical Podcast. Pat (the host) and I discussed a topic I rarely get to talk about: covert key generation. It was a super fun show, and not a topic I get to talk about with many people.
My Thoughts on Pepper Spray
In my recently published on-body EDC items article, I talked about pepper spray. To be honest, I’m very curious by the talismanic quality of The Gun and how many in the self-defense community completely ignore everything else (not all, but many to be sure). If you’re not carrying pepper spray, here are my best arguments to convince you otherwise. You can expect to see more articles about pepper spray here. I am going to do my best to encourage everyone to consider this tool.
EDC Part I: On-Body Carry Items
This post, covering my on-body EDC items, will probably the be the least informative (but most read) of this entire EDC series I’m doing. The reason: there are a million articles out there explaining why you should have an EDC (everyday carry) system. My perspectives on EDC clothing, the EDC bag / bug out bag / get home bag concept, and vehicle preparedness all offer more original ideas than this one. The on-body EDC ground has been well-trod.
State Concealed Carry Class Review
I recently had to attend my state’s concealed carry class. Most concealed carriers don’t get to attend these classes too often. I haven’t attended one in years, but through a bit of a fluke I had to attend one to one to get my current state’s resident permit. I love training, but was I ever disappointed in the class. Today is going to offer an after-action review of my state concealed carry class.
Five Steps to Protecting Your Home Address
Achieving comprehensive personal privacy is a complicated goal involving a lot of complex, discrete steps. On this blog I spend a lot of time focusing on the highly specific, individual steps. Often we fail to provide a lot of context for why we’re doing them, or how they fit into the bigger picture. This was called to my attention recently when an old friend contacted me. He has a legitimate safety reason to wish to be more private, and asked me for advice. Unfortunately, I don’t have a single blog post I could offer him that effectively introduces the basic steps of protecting your home address.
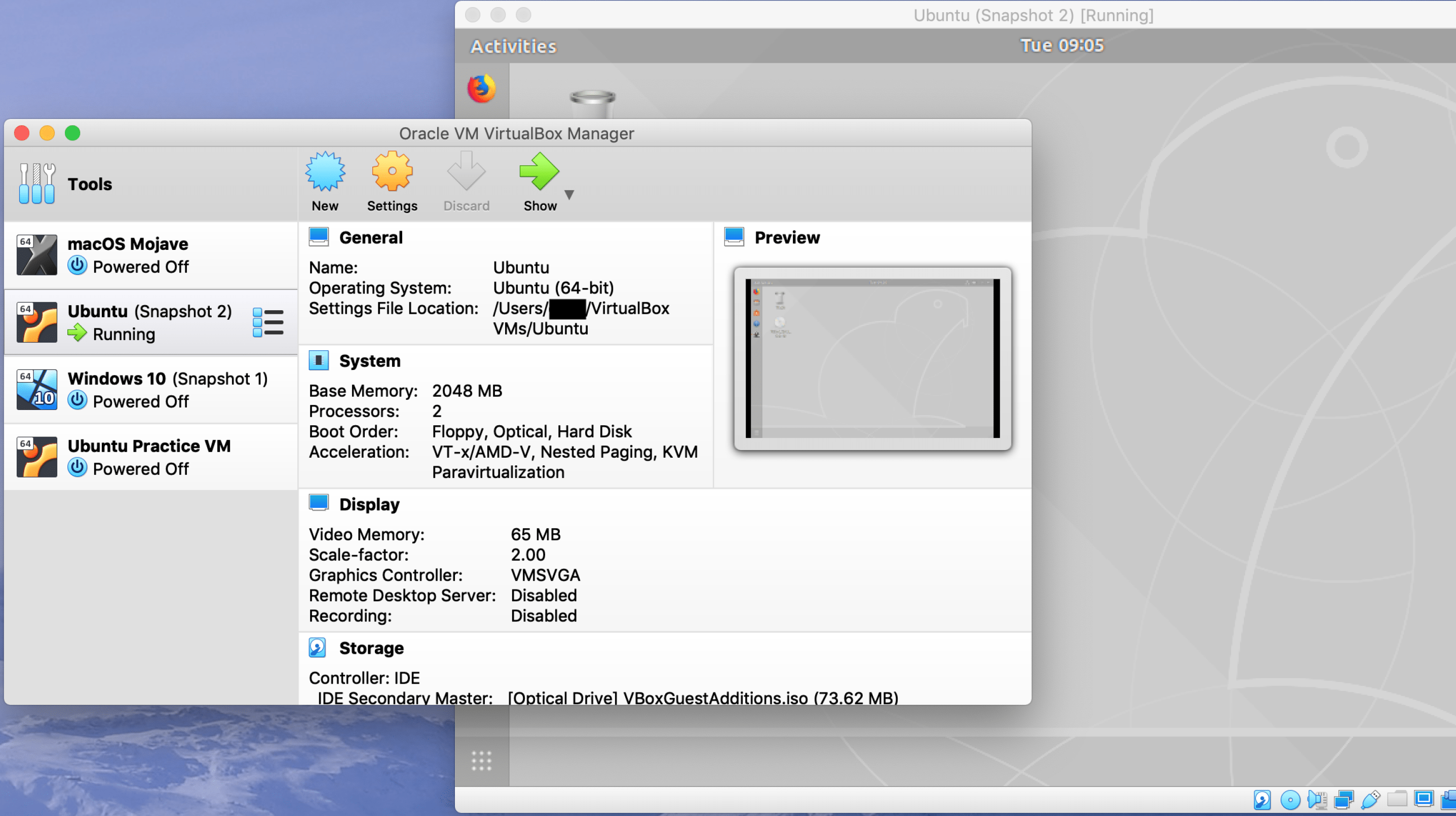
VMs Part III: Snapshot Management
In the last installment in the virtual machine series, I discussed the basic setup of Ubuntu. Today I am going to talk about snapshots, why they’re important, and how to manage them. This tutorial will walk through my workflow for working with snapshots.